File Transfer & Information Security Blog
Featured Articles

-
6 Issues That Sysadmins Should Consider When Everyone is Remote
Michael O'Dwyer | | IT Insights
With ‘social distancing’ a familiar term to most of us at this point, many companies have allowed their employees to work from home, given that the alternative is to cease operations entirely. But it brings a myriad of IT problems.
-
How Hacking, Trolling, and Misinformation Impacts Cybersecurity
The Dark Triad brings together three types of online cyber attacks: hacking, misinformation, and trolling. While they can each work independently, they usually feed off each other and become especially potent when working in concert.
-
Multi-factor Authentication and Single Sign-On for Remote Employees
Greg Mooney | | Security
With entire workforces and student bodies at all levels of education now logging in from home, deploying Single Sign-On and Multi-factor Authentication is as important as ever.
-
How to Pick and Accept a Job Offer
Now, more than ever is a time to learn how to scout for and also choose the best job for you. With the pandemic still raging at the time of this writing, many people are out of jobs and on the hunt.
-
How to Change Registry Permissions with PowerShell
Adam Bertram | | IT Insights | Security
The Windows registry can be a goldmine for attackers and clueless employees. There’s no place better suited for introducing security vulnerabilities or completely screwing up a Windows system than the registry.
-
What Is the Gramm-Leach-Bliley Act (GBLA)?
Greg Mooney | | Security
The Gramm-Leach-Bliley Act (GLBA) has been around since 1999, but it doesn't just affect financial services, it also requires higher education to comply.
-
How To Build Your First GitHub Actions Workflow
In this tutorial, you’re going to learn how to get started with GitHub Actions by creating an Actions workflow to invoke tasks in a job.
-
Six Peer-Reviewed Alternatives to Gartner and Forrester Reports
If you work in IT, or if you're in any position to evaluate and choose IT tools, chances are you're familiar with the names Gartner and Forrester.
-
The Cybersecurity Risks of Remote Employees Working From Home
Greg Mooney | | File Transfer | Security
The latest news and lockdowns around the world may seem drastic to some managers, but the reality is that working from home is the future for all office workers.
-
Podcast: Managing eWaste in a Secure and Compliant Manner
Greg Mooney | | Security
Businesses must consider all the data security implications when dealing with eWaste. Many companies are now opting to shred old equipment on top of using tools to wipe storage devices.
-
4 Basics of Identity Access Management (IdAM or IAM) that IT Pros Should Know
Michael O'Dwyer | | IT Insights | Security
Call it Identity Management (IDM), Identity Access Management (IdAM), or even IAM; IT is responsible for its implementation and ongoing maintenance.
-
What is the HIPAA Omnibus Rule?
Greg Mooney | | Security
In this article, we discuss what the HIPAA Omnibus Rule is and how it relates to HIPAA and HITECH.
-
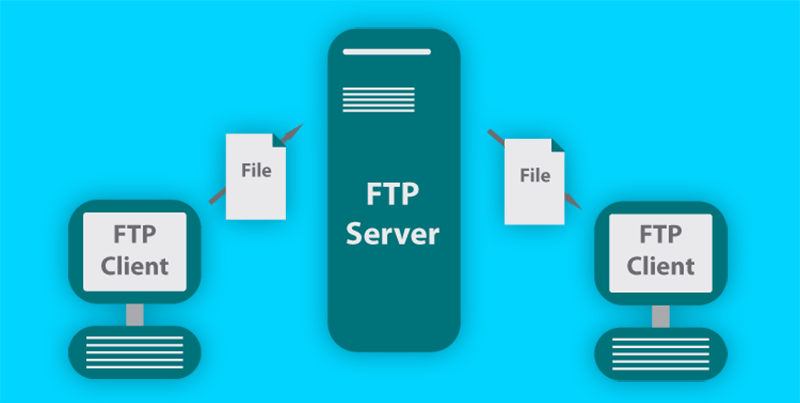
What is file transfer protocol (FTP)?
Greg Mooney | | File Transfer | Security
At its simplest, File Transfer Protocol (FTP) is a rudimentary method of moving files from one location on a network to another.
-
Getting Started with Azure Bastion
Azure Bastion can best be described as a managed jump host. A jump host, also called a jump box, is a virtual machine that's placed on a virtual network. This article describes how to get started with Azure Bastion.
-
Configure 'Break Glass' Emergency Access for Azure Active Directory
In cloud computing generally and in Microsoft Azure specifically, the shared responsibility model means that both Microsoft and you (the customer) have a role to play in ensuring service high availability.
-
Do You Need To Comply With CCPA If You Are HIPAA Compliant?
Michael O'Dwyer | | IT Insights
Disclaimer: This post should not be used to determine your CCPA obligations and does not offer legal advice. It is designed to inform, raise some questions and lead you to investigate further by consulting with attorneys with relevant experience in data privacy laws and...
-
How to Automate an Azure Lab Setup
In this article, I’m going to show you how you can build an entire Azure lab setup with a single line of PowerShell.
-
Managed File Transfer (MFT) vs. File Transfer Protocol (FTP)
Greg Mooney | | Security
This article provides the detailed features comparison needed when the need for file transfer moves from occasional to operational.
-
What is HITECH?
The Health Insurance Portability and Accountability Act (HIPAA) was introduced in 1996, and compliance was (and indeed is) necessary for all U.S. healthcare organizations.
-
Getting Started with Azure Firewall
Tim Warner | | Cloud | IT Insights
In today's tutorial, I'll teach you how to get started with Azure Firewall, Microsoft's cloud-native managed firewall appliance. Call it firewall-as-a-service if you'd like. Let's begin!