File Transfer & Information Security Blog
Featured Articles

-
Bring Some Turkey to the Server Room This Thanksgiving
With the holiday’s right around the corner, it is time to give thanks for the people that are really important in your life—like your SysAdmin.
-
Libra Is A Good Idea On Its Own, But Not With Facebook
Michael O'Dwyer | | IT Insights
Mark Zuckerberg is still pushing for the creation of Libra, but it's obviously futile for him at this point. He knows we don't trust Facebook.
-
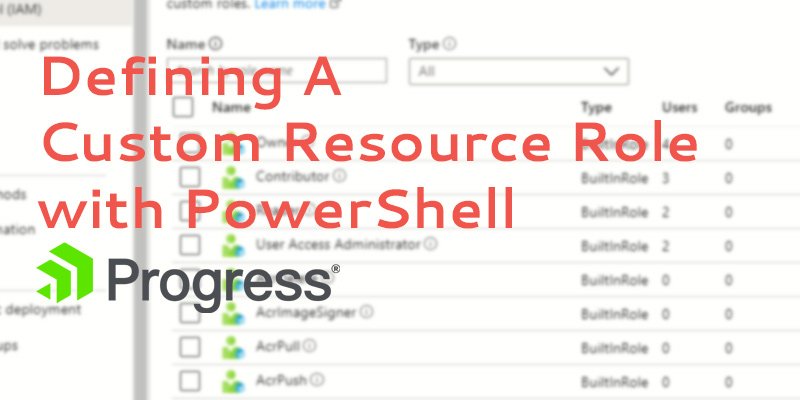
How To Define a Custom Azure Resource Role with PowerShell
In this post, PowerShell expert Tim Warner shows you how you can create a custom Azure Resource Role with PowerShell.
-
How to Define a Custom Azure AD Role in the Azure Portal
We've been able to define custom Azure resource roles for awhile now. Today I'll teach you how to create a custom Azure AD role.
-
AS2 vs. SFTP: Which is Best for You?
Jeff Edwards | | Security
There are lots of file transfer protocols to choose from, but one that’s rarely discussed in depth is AS2. In this article, we take a deeper look at AS2, how it stacks up against SFTP, and why you would choose one or the other.
-
Get-CIMInstance Vs Get-WMIObject: What’s The Difference?
PowerShell provides two similar management interfaces for accessing data on a computer: WMI and CIM.
-
Podcast: IT Horror Stories
In this podcast, we hear from a few IT experts about the worst IT nightmares they've ever encountered.
-
Why Retailers Are a Soft Targets to Hackers (And What to Do About it)
Jeff Edwards | | IT Insights | Security
Time and time again, retailers prove to be a popular (and easy) target for hackers. The tangible and intangible costs for an e-commerce site that’s been breached can escalate quickly. In this post, we'll explore the issue, and outline some solutions.
-
Managing Azure Blueprints with PowerShell
Azure Blueprints provide a "one-stop shop" for Azure governance. By implementing JSON templates and a controlled, unified workflow, Azure administrators can define, deploy, enforce, and maintain standardized Azure environments.
-
Searching Active Directory with PowerShell
Dan Franciscus | | IT Insights
For many Microsoft IT professionals, one of the first things they do with PowerShell is using it to perform tasks in Active Directory.
-
PCI DSS Compliance 101: What You Need to Know
Jeff Edwards | | IT Insights | Security
If your business deals with credit card payments in any way, then PCI compliance is going to be a fact of life, and an essential part of running your business securely and efficiently. PCI compliance is a critically important step in protecting your customer's or...
-
Provide High Availability for Azure AD Connect
Once you start rolling with Azure AD Connect and hybrid identity between local Active Directory and Azure Active Directory, one of your first thoughts is, "What happens if my Azure AD Connect server goes offline?"
-
4 Myths of PCI Compliance
Greg Mooney | | Security
If your organization is finding it difficult to comply with PCI DSS, the Payment Card Industry Data Security Standard, it could be due to some of the misconceptions about the standard.
-
Deploy a Managed Storage Account in Microsoft Azure
Today I will teach you how to create what Microsoft calls a managed storage account. As you may know, each storage account has two interchangeable private keys you can use to authenticate programmatically to the general purpose storage account's four services:
-
Using Invoke-Command in PowerShell
Dan Franciscus | | IT Insights
In this article, Dan Franciscus covers how to use the Invoke-Command and why it is one of his favorite commands to use in PowerShell.
-
SSL 101: SSL/TLS Certificates And Why You Need Them
Secure Socket Layer (SSL) or Transport Layer Security (TLS) refer to security technologies that encrypt data sent between a web server and web browser.
-
Podcast: Have You Met? Orsenna
We recently had a chance to sit down with Progress' partner, Orsenna, who has been serving WhatsUp Gold customers in Europe. More specifically, Switzerland.
-
How to Lower the Risk of Employee Data Theft
As IT pros, we’ve been aware for quite some time that some users are a threat to security, whether by their use of shadow IT, their susceptibility to social engineering attacks from cybercriminals, or by using their employee role and access permissions to compromise data...
-
Four Chocolatey Security Features
Dan Franciscus | | IT Insights | Security
The process of securely installing software in Windows is something that IT professionals grapple with, especially in an enterprise setting.
-
Why you Shouldn’t Use FTP to Transfer Cloud Files
Jeff Edwards | | Cloud | File Transfer | Security
The cloud is a fact of life in 2019. From basic cloud collaboration tools to storage buckets on massive cloud platforms like Azure and AWS, most businesses perform thousands of cloud file transfers every day, whether they’re aware of it or not. For businesses and IT...