File Transfer & Information Security Blog
Featured Articles

-
3 Data Backup Tools Worth Considering
Michael O'Dwyer | | IT Insights
If you are a small or medium business, you may have left your data backups in the hands of outside help or, even worse, to chance.
-
Podcast: Information Governance Report
When it comes to cost savings for IT operations and businesses in general, information governance is probably the last thing you think of. In this podcast, we discuss the implications of information governance.
-
Measuring Reboot Time with PowerShell
Dan Franciscus | | IT Insights
In enterprise environments, you will usually find an array of different Windows operating systems, hardware and of course software. Typically, machines are managed and configured with group policy and SCCM, or perhaps other more modern methods like Chef or Puppet. One of...
-
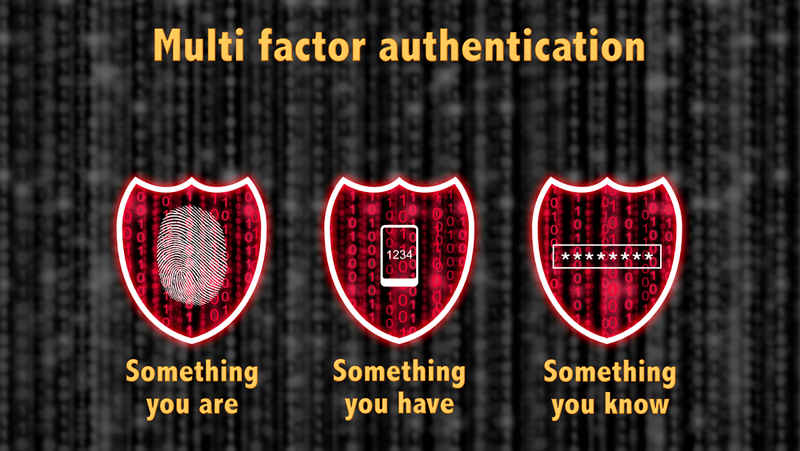
Passwords Don't Work: Multi-Factor Authentication is Essential
Mark Towler | | Security
A month ago we told you how MFA (Multi-Factor Authentication) is an essential part of your encryption strategy. This month we’re letting someone else tell you the same thing for even more confirmation.
-
Why Auditable Access Controls Matter
Jeff Edwards | | File Transfer | Security
By now, you should know that controlling access to sensitive files, devices, tools, and network areas is of utmost importance in cybersecurity, but you should also know that it’s not enough to simply control how users access resources. It’s equally important to be able...
-
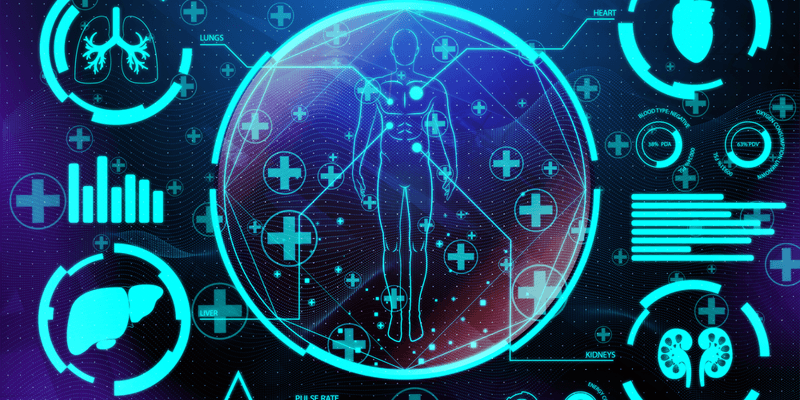
APIs Provide the Data Access Windows for Improving Healthcare
Greg Mooney | | IT Insights | Security
APIs are becoming a huge part of how healthcare organizations provide better care to patients. But what about the security concerns with APIs?
-
Top IT Security Certifications to Elevate Your Career
Greg Mooney | | Security
Nobody does IT security better than you and your InfoSec team. You developed a strategic plan that prevents most breaches, and for those that do slip by your perimeter defenses, you have a great tactical plan to identify and mitigate attacks as quickly as possible....
-
Global Data Privacy Laws: US, EU, China and More
Sherwood Stranieri | | IT Insights
In the 2018-2020 timeframe, the rollout of GDPR in the EU is having an impact on companies worldwide, thanks to its legislative reach beyond the EU’s borders. But companies also have to content with a wave of new data privacy legislation in the US, UK, China, and many...
-
Enforcing Security Policy Agreement at Sign On with MOVEit
Mark Towler | | Security
Security policies are prone to change, and you need to keep your users up-to-date on those changes so that they won't violate the terms of the policy, but doing so is often easier said than done.
-
Introduction To The New Windows Terminal
Dan Franciscus | | IT Insights
Recently at the Microsoft Build conference, it was announced that there is a new Windows terminal that can be used as an alternative to cmd of PowerShell, called Windows Terminal.
-
Why Balancing Access Controls for Managed File Transfer Matters
Jeff Edwards | | File Transfer | Security
If you're using secure file transfer tools, chances are you're security conscious. Maybe you're working in a highly-regulated industry, or perhaps you don't want your company on the front page of the newspaper for getting hacked. Whatever the case, if you're securing...
-
Why Email and EFSS are Unsecure
Greg Mooney | | Security
FTP (File Transfer Protocol) has been the standard bearer for sending or moving files too large for email. Today, those file transfers contain the lifeblood of an organization and so Secure FTP is now critical.
-
Podcast: Why You should Archive Data Today and in The Future
Jeff Edwards | | File Transfer | Security
Businesses archive their data for a lot of reasons, but what is the most critical use case for archiving? For security or for posterity?
-
Bluetooth Security Problems: A Cause For Concern
Michael O'Dwyer | | IT Insights | Security
Bluetooth security… Some consider it an oxymoron, like ‘global intelligence’ community or ‘offshore support’ while others recognize Bluetooth flaws and understand their causes. Whatever side of the fence your opinions lie, it’s fair to observe that Bluetooth has its...
-
Announcing MOVEit 2019.1, with Permission Configuration and Multiple Server Support
Jeff Edwards | | File Transfer | IT Insights
Progress and Ipswitch are proud to announce the release and general availability of MOVEit 2019.1, the newest iteration of the industry leading MOVEit secure managed file transfer (MFT) solution used by thousands of IT professionals to provide complete visibility,...
-
Podcast: Have You Met? QBITS
Greg Mooney | | Security
In this Have You Met? podcast, we sat down with Daniel Hotz of QBITS, a Progress partner based in Switzerland, to see how they are implementing MOVEit managed file transfer in the various regions they serve clients.
-
Peer-to-Peer File Transfer: How to Protect Your Sensitive Data
Greg Mooney | | Security
Efficient collaboration and peer-to-peer file transfer are important for any job, but you don't want to do it in a way that leaves data unprotected.
-
Using Make Me Admin for Administrator Privilege
Dan Franciscus | | IT Insights | Security
In this article, we discuss how to grant users simple admin rights temporarily like installing software. This helps keep IT from getting bogged down.
-
The Difference Between PGP, OpenPGP, and GnuPG Encryption
Greg Mooney | | Security
Ah, cryptography. It’s so important to us in our every day lives and yet it has one of the longest and confusing pasts of any type of technology we use today.
-
Why Your Encryption is Only as Good as Your (Multi-Factor) Authentication
Jeff Edwards | | Security
Username and password may be the de-facto means of authentication for many organizations, but they can easily be the weakest link in security controls. In this article, we’ll detail why Multi-Factor Authentication (MFA) should be paired with encryption for top-level...