File Transfer & Information Security Blog
Featured Articles

-
How to Search Windows Event Logs Across Hundreds of Servers
Adam Bertram | | Security
The Windows event logs are a great place to start when troubleshooting problems or investigating potential security breaches.
-
Top 5 Types of Mobile Device Breaches
Mobile devices are one of the weakest links in cyber security for businesses, yet very little is being done to mitigate the risks around these top 5 types of mobile device breaches.
-
Podcast: Have You Met? David Perkins, Level 8 Solutions
Level 8 Solutions called into the Defrag This - Have You Met? podcast studio to provide some insight into how they are implementing IT solutions in the UK.
-
Everything You Need to Know About China's Cybersecurity Law
Jeff Edwards | | IT Insights | Security
In this article, we'll answer some of the most common questions about the CSL, and make compliance goals as clear as possible.
-
Using Zapier to Automate Common Business Workflows
Adam Bertram | | Automation | IT Insights
A typical company has thousands of workflows happening all of the time, whether it's onboarding new employees, approving expense reports or opening up a helpdesk ticket.
-
The Biggest Security Risks of Using 3rd Party APIs
Businesses have steadily improved their perimeter security to better protect against an ever increasing number of cyber attacks. This has left hackers to look for other, less challenging paths to an enterprise’s data in 3rd party APIs.
-
MiFID II: What IT and Compliance Teams Need to Know
Greg Mooney | | IT Insights | Security
MiFID II signifies the continuing onslaught of financial market regulations that demand transaction transparency. Such regulations burden compliance and IT teams who have to ensure their companies meet increasingly stringent security standards.
-
HIPAA Compliance & Managed File Transfer: Do You Have a Safety Net?
Security breaches are occurring at an alarming rate as cybercriminals continue to successfully infiltrate the IT infrastructures of organizations across many industries.
-
How to Validate Infrastructure Changes Using PowerShell Pester Tests
Adam Bertram | | Automation | IT Insights
Changes can make infrastructure better or can bring it to its knees. Change management is a crucial part of managing infrastructure in an IT pro’s world. When you do make changes, are you sure you changed the right setting? Are you sure that change you made didn’t affect...
-
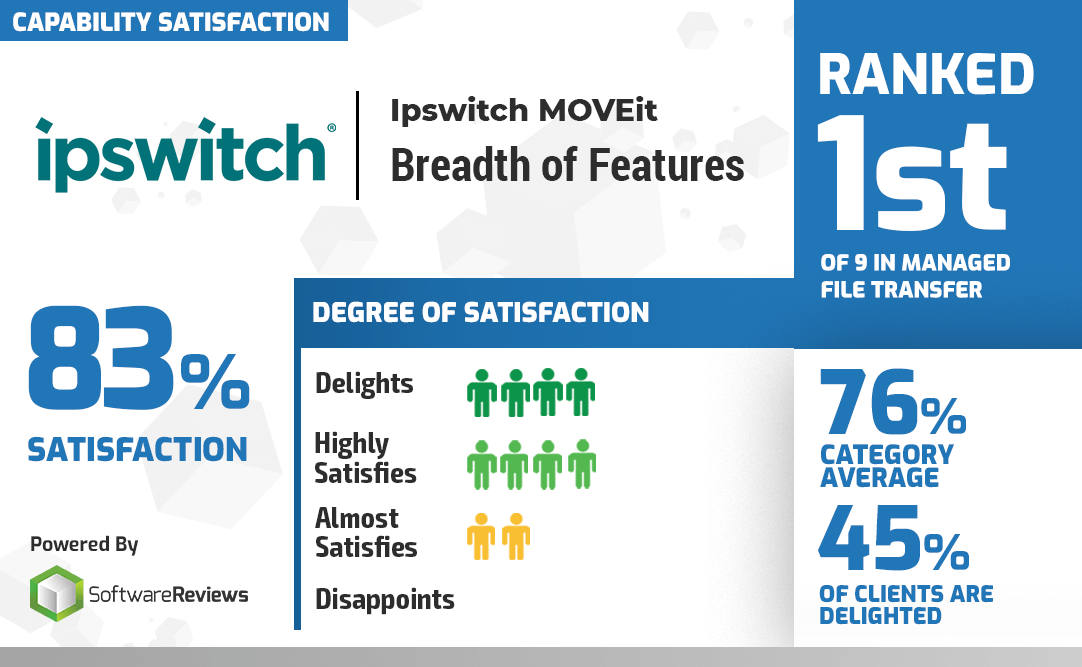
MOVEit Named Data Quadrant Gold Medalist in Info-Tech MFT Category Report
Jeff Edwards | | File Transfer | IT Insights
We’re proud to announce that Software Reviews, a division of research and advisory firm Info-Tech Research Group Inc., has named MOVEit® managed file transfer software as a Data Quadrant Gold Medalist in their new Managed File Transfer Category Report.
-
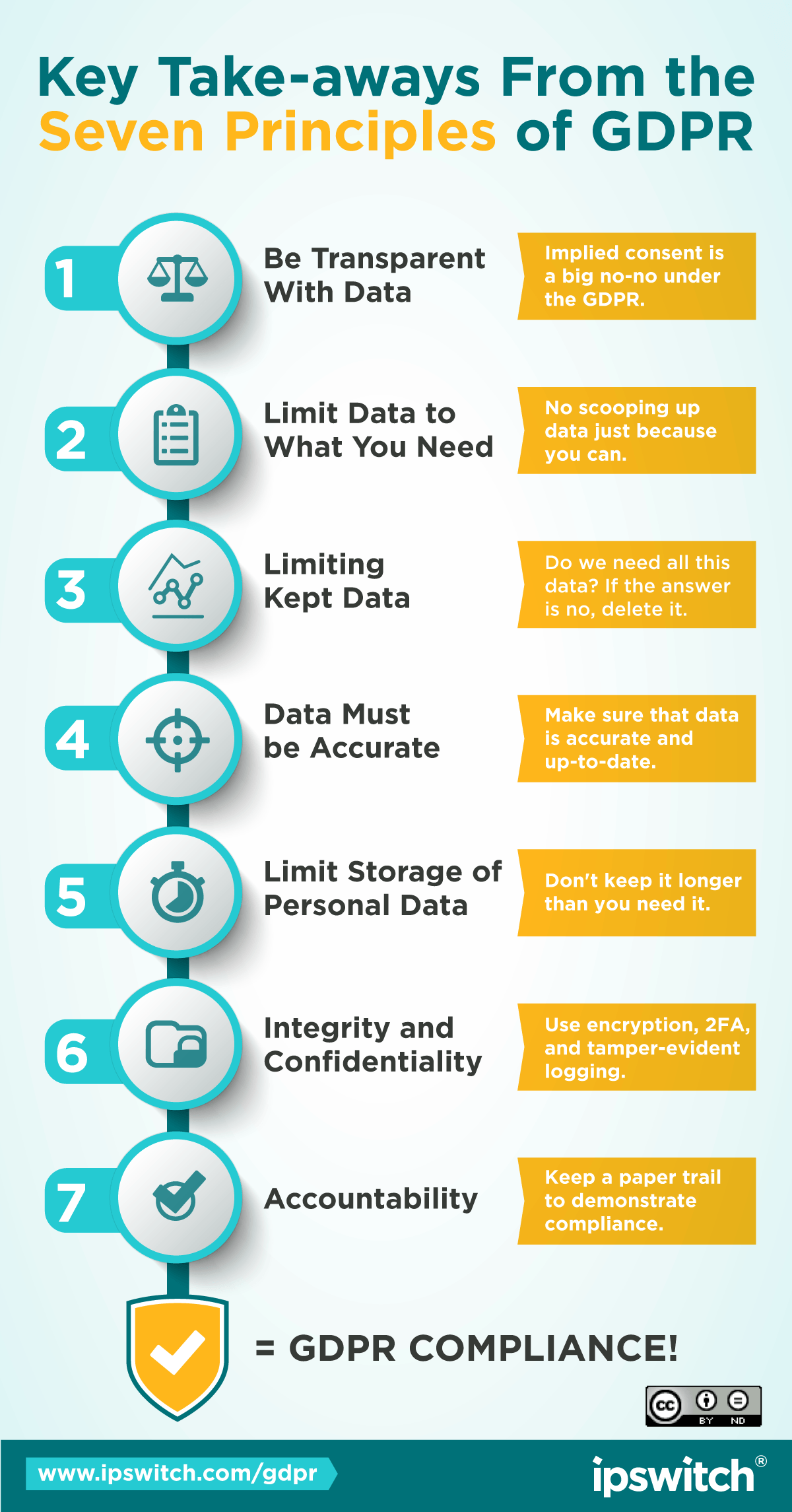
GDPR Overview: Complying with EU Laws for Personal Data
Jeff Edwards | | IT Insights | Security
With the EU’s General Data Protection Regulation (GDPR) now in effect, GDPR preparedness should be top of mind for businesses everywhere, not just those based in the European Union (EU). This GDPR overview will take you through the basics, including the seven principles...
-
How to Create and Configure an AWS VPC with Python
Prateek Singh | | Automation | IT Insights
Amazon Web Services enables you to create a custom defined virtual network also know as Amazon VPC or Amazon Virtual Private Cloud, which, just like any traditional network in a data center, is highly scalable and easily configurable using programming languages like...
-
What is API Management?
Application programming interfaces, otherwise known as APIs, are an important aspect of any piece of software or platform. If you think about all the data that passes through an application these days, it is hard to think of a time when APIs weren’t an integral part of...
-
UK Government Orgs. Aren’t Updating Email Security, Survey Finds
Jeff Edwards | | File Transfer | IT Insights | Security
Just 28% of gov.uk domains have implemented new email security standards from the Domain-based Message Authentication, Reporting and Conformance (Dmarc) protocol, according to a study from data security company Egress.
-
Podcast: New MOVEit Integration Available on MuleSoft AnyPoint Exchange
Greg Mooney | | Security
I got a chance to sit down with Kevin Conklin, the VP of Marketing at Ipswitch to talk more about the new MOVEit 2019 release and how the new MOVEit is now integrated with Mulesoft’s Anypoint Exchange.
-
What The Heck is iPaaS? Do You Need an iPaaS Provider for File transfer?
Ah, the cloud. It's changing the face of IT forever, and while it's at it, it's providing us with a never-ending stream of acronyms.
-
Announcing the New MOVEit 2019, With Enhanced Security and Native Support for Azure BLOB Storage
Mark Towler | | File Transfer | IT Insights
We're excited to announce the latest version of our managed file transfer (MFT) solution, MOVEit 2019! We’ve included a bunch of new features that make it easier to use, provide more flexible security options and make scaling to cloud services like Microsoft Azure...
-
Why IT Won’t Let You Use Online File-Sharing Services
IT keeps schooling you about the dangers of Dropbox, Google Drive, OneDrive, and other online file-sharing services. But you still need to collaborate with your colleagues as well as your customers and business partners.
-
How MuleSoft Certified Connector for MOVEit Transfer Makes File Transfer Secure and Painless
John Picinich | | Automation | File Transfer | IT Insights
Ipswitch has recently released its new MOVEit Transfer connector to MuleSoft’s Anypoint Exchange. This connector will enable MuleSoft customers to easily integrate secure managed file transfer capabilities into their Mule applications, leveraging the power of Ipswitch’s...
-
How to Automate AWS S3 Static Websites Using Python
Prateek Singh | | Automation | IT Insights
Amazon Web Services offers a very popular object storage service known as Amazon S3 (Simple Storage Service) that enables you to store data, files, images and even videos in highly available containers called ‘buckets’ which are also easy to access endpoints using any...