File Transfer & Information Security Blog
Featured Articles

-
Podcast: API Security in the Cloud
Greg Mooney | | Cloud | Security
Too many IT professionals believe that companies that provide cloud platforms and services, such as AWS or Google Cloud, handle all the cloud-related security. Considering how much business transpires in the cloud, this is a dangerous assumption to make.
-
Marriott Hotels Discloses Data Breach Affecting 500M Customers
Jeff Edwards | | Security
Today, the world's largest hotel chain, Marriott International, disclosed what may be turn out to be one of the largest data breaches in history.
-
File Transfer Tools Can Lead to GDPR Non-Compliance
Greg Mooney | | Security
It’s the proverbial 1,000-pound gorilla—a compliance violation. Perhaps you haven’t seen one yet, but you know it’s out there lurking, and it just might come banging on your door any day now.
-
How to Detect and Stop Cryptomining on Your Network
Jeff Edwards | | Security
If 2017 was the year of the ransomware attack, then 2018, insofar as it can be defined by malware, was the year of cryptojacking.
-
Is Running A Virtual Machine (VM) Worth The Effort?
Michael O'Dwyer | | IT Insights
In the computing world, virtualization by way of virtual machines is used to describe a method of avoiding the purchase of multiple physical computers or servers, one for each operating system.
-
Create Windows Machine Builds with Packer
Dan Franciscus | | IT Insights
While it supports Windows and Linux, creating an OS image is vastly different between the two. In this article, I will focus on how Packer is used for Windows OS image creation.
-
How to Increase Collaboration Without Reducing Security
Jeff Edwards | | File Transfer | Security
Collaboration is of utmost importance in the modern workplace, but when done incorrectly, a collaborative environment can also be an insecure one. Here's how you can allow increased workplace collaboration, without reducing security.
-
Podcast: Shadow IT Problems & Solutions
Shadow IT is a real problem in the modern workplace. In this episode of Defrag This, we explore the reasons users turn to the dark side, the risks of unsanctioned IT stacks, and some of the solutions IT teams can use to curb Shadow IT.
-
Import Machine Images Into AWS with Packer
Dan Franciscus | | Cloud | IT Insights
Amazon Web Services (AWS) is still the most popular cloud platform and Packer provides great integration that enables users to import builds into AWS and convert them to Amazon Machine Images (AMI).
-
The Ghost in the Machine – A Spooky Short Story About a Sysadmin
Edgar Allan Mooney | | IT Insights
Once upon a blood moon, there was a sysadmin called Kyle and he almost lost it all to the ghost in the machine...
-
Safeguarding Your Network From Insider Threats
Nate Lewis | | File Transfer | Security
"The call is coming from inside the house...” This line from 1979’s When a Stranger Calls terrorized audiences by introducing the notion that the things we should be most fearful of may be in the spaces we feel most safe. This idea translates neatly to the enterprise...
-
Benefits of Managed File Transfer for Banking and Finance
In the BFSI (banking, financial services and insurance) industry, choosing a managed file transfer solution is rather simplified as FTP alone is not enough to meet the necessary regulatory and compliance requirements.
-
How to Run Commands on Remote Computers with PowerShell
Adam Bertram | | Automation | IT Insights
Running commands locally on the remote computers is a common task many IT admins have to do every day. Here's how you can do that in PowerShell.
-
Balancing Security and Ease of Use with Two-Factor Authentication
Username and password have long been the main method of authentication—and they remain so. But other authentication factors are often added to passwords to improve security. How well do these multi-factor authentication approaches work, and should businesses approach...
-
Which Secure File Transfer Solution Is Right for You?
You likely already realize that file transfers using the file transfer protocol (FTP) expose your sensitive data to high risks.
-
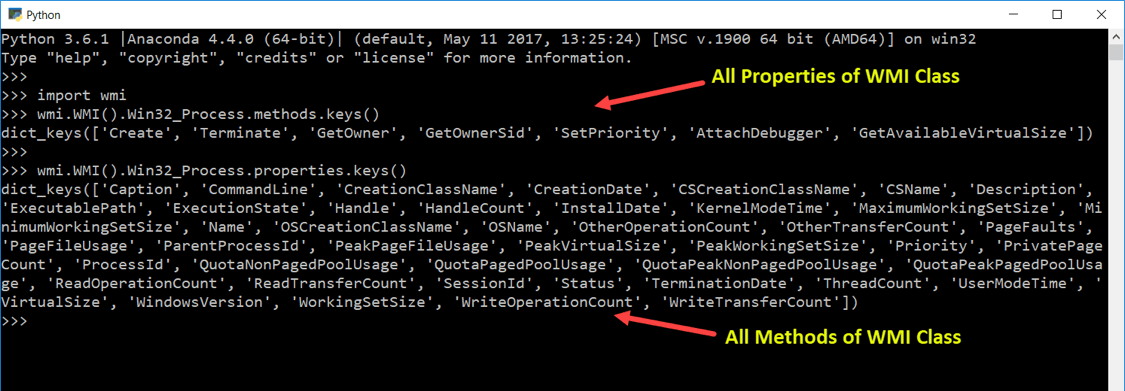
Managing Windows System Administration with WMI and Python
Tired of managing Windows system administration tasks manually? Wish you could set up a few Python scripts instead? Where there's a will, there's a way! In this article, we'll show you how to install Python's WMI module and how you can use it to perform system...
-
How to Manage AWS IAM Users with Python
Prateek Singh | | Cloud | IT Insights | Security
Amazon Web Services (AWS) offers a service known as Identity and Access Management (IAM) that lets AWS Administrators provision and manage users and permissions in AWS cloud. AWS IAM can prove very useful for System Administrators looking to centrally manage users,...
-
What you Need to Know About FIPS 140-2 Validation
Nate Lewis | | Security
One look at the headlines is all it takes to see why security is at the forefront of every IT team’s mind. Hacks, data theft—you name it; some of the largest corporations have succumbed to these pitfalls over the past few years, and there’s no end in sight. It's no...
-
Internet of Things 101 – IoT Device Authentication Explained
Readers of previous posts are aware of my reservations on the current ubiquitous drive to connect absolutely everything (from the frivolous to the useful) to the internet but there is no denying that the trend will continue unabated. This will create security risks that...
-
How to Manage AWS EC2 Infrastructure with Python
In this article, we'll take a look at how system administrators can use Python to manage their Amazon Web Services (AWS) Elastic Compute Cloud (EC2) infrastructure. You’ll learn to query existing EC2 instances, change the state of the virtual machines and their...