We've been able to define custom Azure resource roles for awhile now. Today I'll teach you how to create a custom Azure AD role.
Azure Resource Manager (ARM) uses role-based access control (RBAC) to authorize access to Azure AD and Azure subscription resources. A role is a named permissions collection that is associated with a particular job role.
Microsoft gives us several built-in RBAC roles Azure AD and Azure resources, but we can define custom RBAC roles if we need more granular access than what the built-in roles provide.
We've been able to define custom Azure resource roles for awhile now. Today I'll teach you how to create a custom Azure AD role.
Inspecting Build-In Azure AD Roles
Let's begin by taking a peek behind the proverbial curtain to see how Microsoft composes the Azure AD built-in roles. Log into the Azure portal with an administrative account, browse to your Azure AD tenant, and select the Roles and administrators setting. From there, select the User Administrator role. Finally, click the Description setting. I show you this interface in Figure 1.
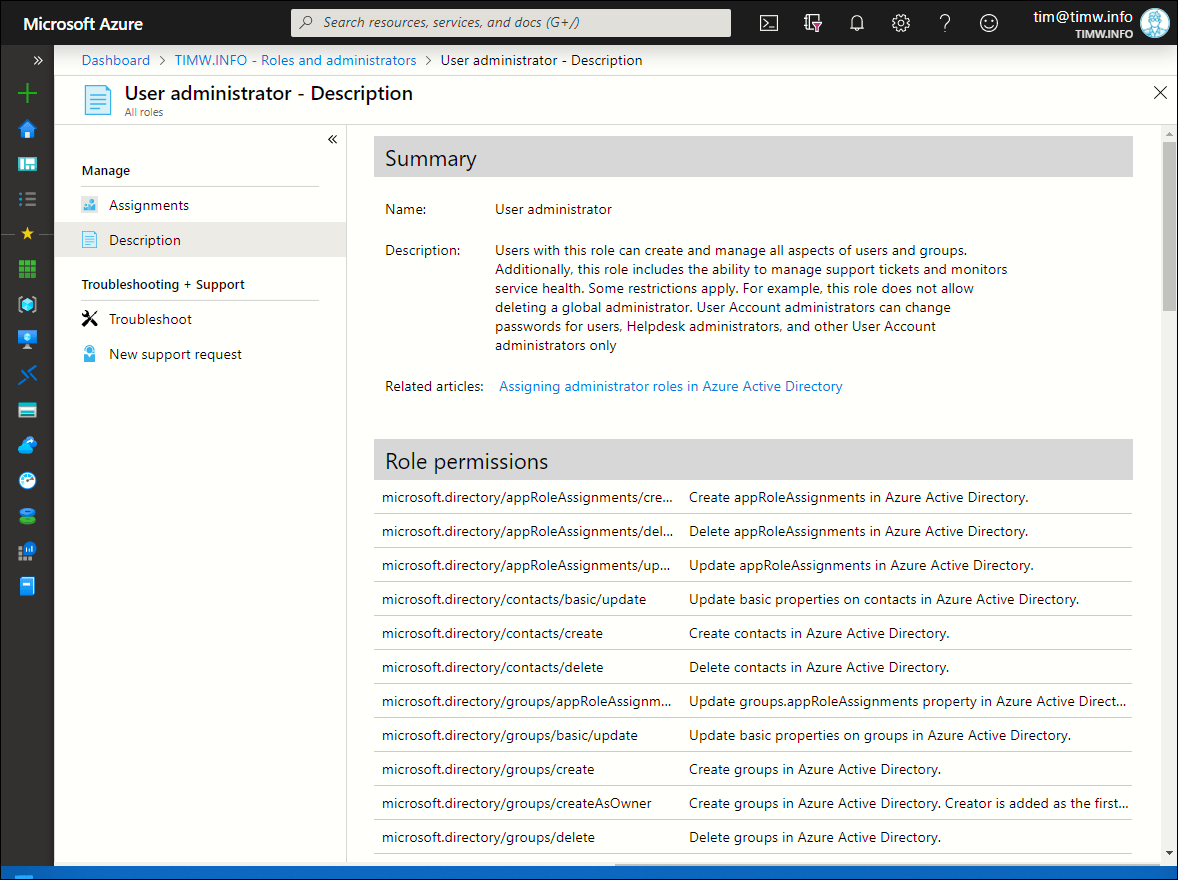 Figure 1. Inspecting a built-in Azure AD RBAC role.
Figure 1. Inspecting a built-in Azure AD RBAC role.
Under Role permissions you see all the ARM resource provider operations included in the User administrator role. The following three operations enable the role holder to create, update, and delete Azure AD groups, respectively:
- directory/groups/create
- directory/groups/basic/update
- directory/groups/delete
You should copy any operations that you may want to include in a custom Azure AD role.
Creating a Custom Azure AD Role
Let's define a custom role called App Owner Administrator that gives role holders the ability to update the owner of Azure AD-registered applications.
As of this writing in October 2019 Azure supports only application registration-related permissions for Azure AD custom roles. In time, we'll be able to include all Azure AD permissions operations in our role definitions.
Your Azure AD account needs to be either a Global Administrator or Privileged Role Administrator role holder to create custom Azure AD roles.
Navigate back to the Roles and administrators blade and click New custom role to get started. Fill in the Basics blade (shown in Figure 2) with the custom role name and description. In this case we have to start from scratch; once you have at least one custom role defined you can use it as a template from which to define a new role.
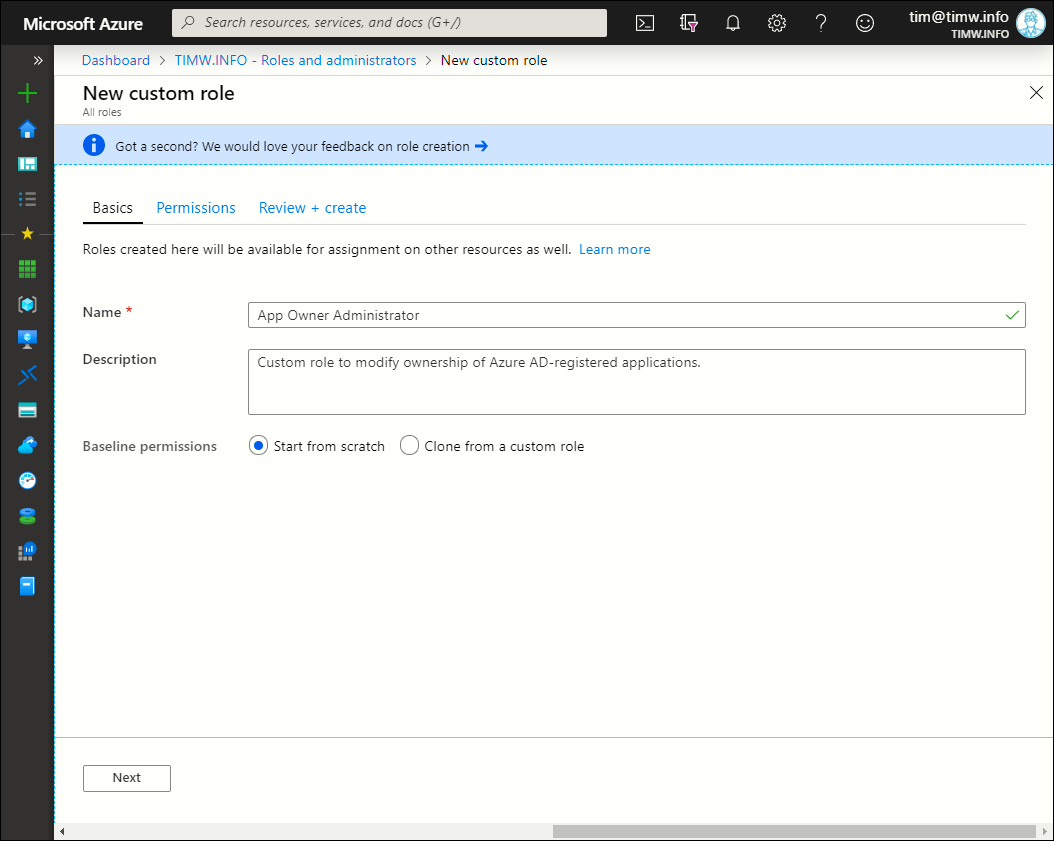 Figure 2. New customer role Basics blade.
Figure 2. New customer role Basics blade.
Next comes the difficult part. On the Permissions blade, use the Search by permission name or description box to find the permission operations you want to include in your role. I show you the interface in Figure 3.
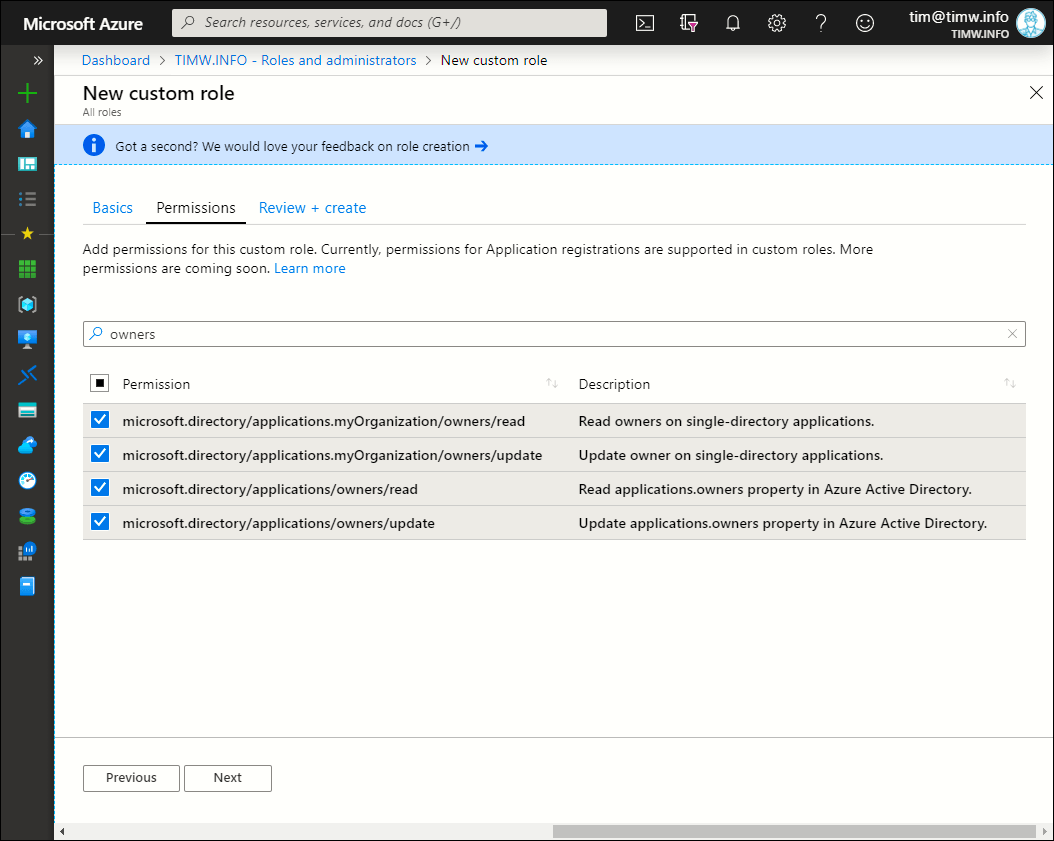 Figure 3. Adding permission operations to the custom role.
Figure 3. Adding permission operations to the custom role.
Please understand that custom role creation is a time-consuming and iterative process. You'll likely find that you need to test the role over and over again until you get the permissions list correct. I suggest you open a second browser tab in which you do your testing.
Click Next and then Create to complete the App Owner Administrator custom role definition.
Assigning The New Role
Browse to your Users blade and select an Azure AD user who will serve as your test account. In the user's profile, select Assigned roles and assign the user the App Owner Administrator custom role. In my environment, I assigned my fictional user Anna Brinkley to the role (Figure 4).
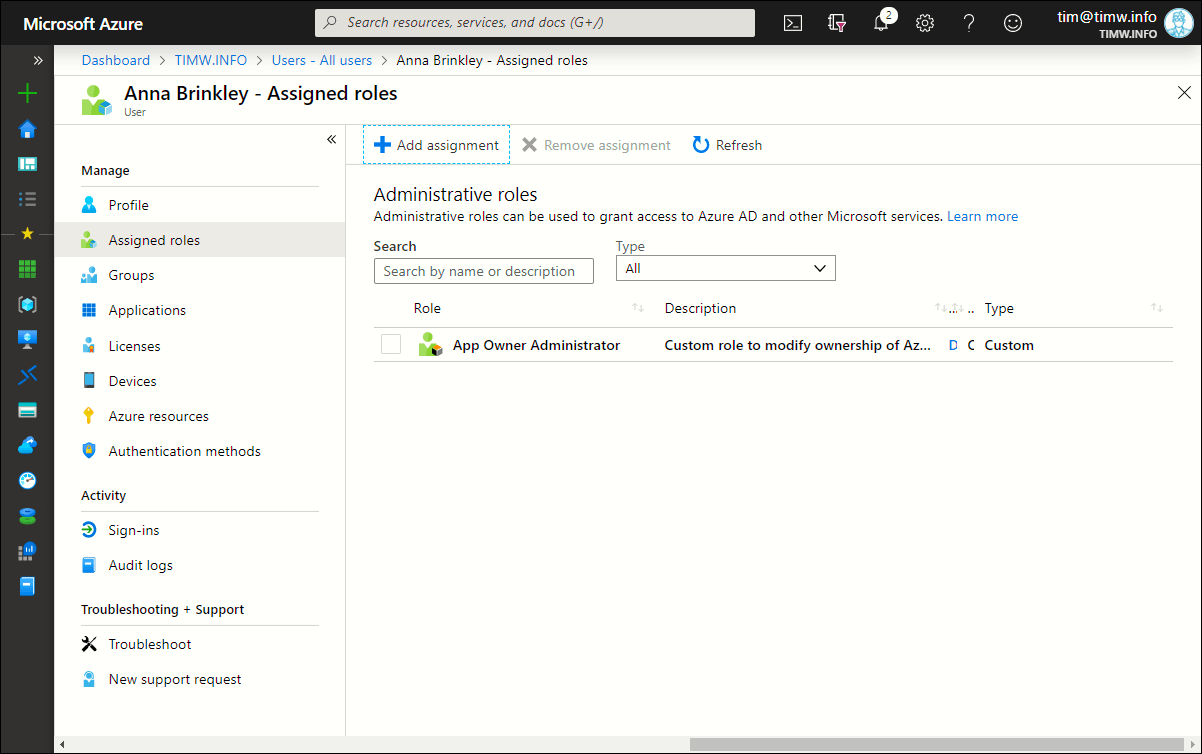
Figure 4. Assigning the custom role to an Azure AD user.
Testing the New Role
Open another browser tab (preferably using Incognito, InPrivate, or whatever your browser calls a private session) and log into Azure portal as the test user. Once logged in, open Azure AD and browse to the Users tab. This user should have no other Azure roles assigned, so he or she should not be able to, for instance, create user accounts. You can see this feature (called "security trimming") in Figure 5.
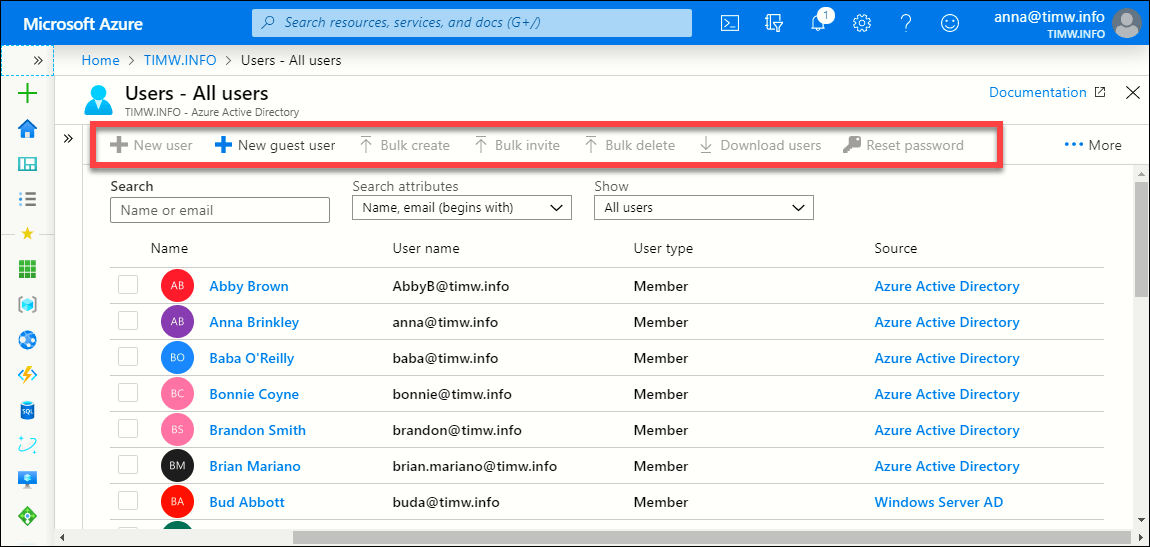 Figure 5. Azure RBAC prevents administrative actions that are not explicitly allowed via role membership.
Figure 5. Azure RBAC prevents administrative actions that are not explicitly allowed via role membership.
Finish by browsing to the App registrations blade, selecting a cloud app, and selecting the Owners setting. As shown in Figure 6, the custom role holder should be able to update this property value.
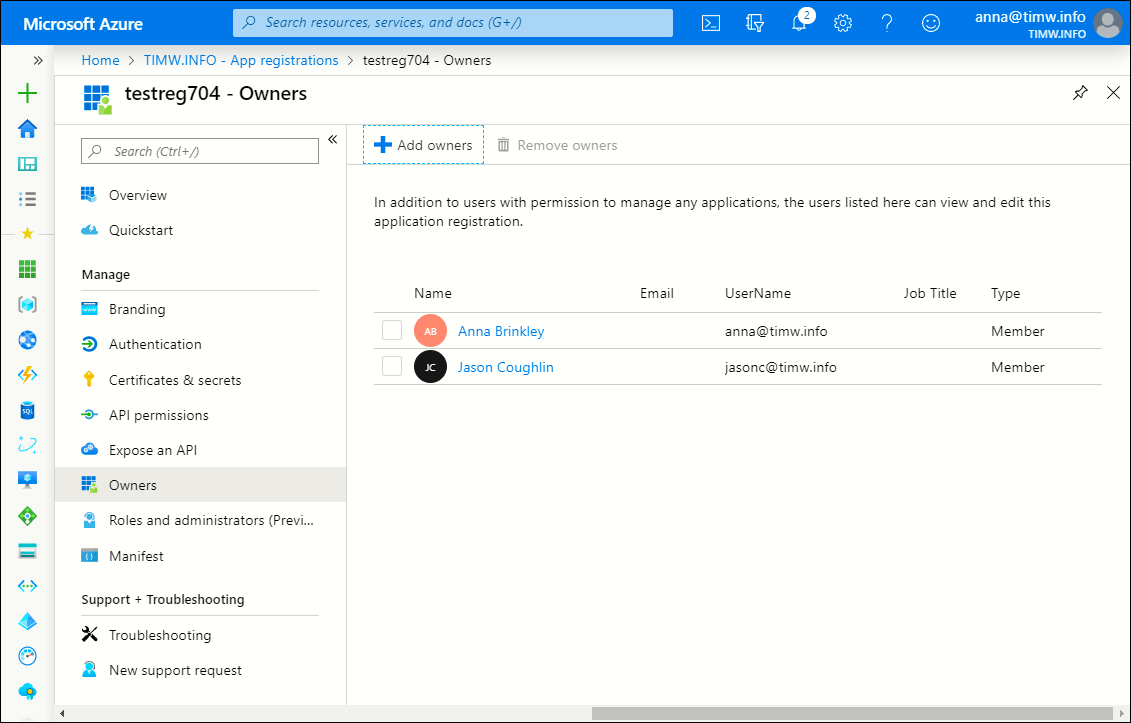 Figure 6. The custom Azure AD role works as expected.
Figure 6. The custom Azure AD role works as expected.
Wrap-Up
There you have it! Custom role support for Azure AD has been a long time coming, and I'm so glad Microsoft is taking action on this. As I mentioned, we'll see greater permissions coverage for this over time, so keep your eyes on the feature.
