Network Discovery Tools
Layer 2/3 Discovery, Mapping, Inventory and IT Asset Reporting
Discover, Map and Monitor Your Network Devices in Minutes
Discover everything connected to your network from devices, servers, deployed software, Windows, wireless and virtual infrastructures and more. WhatsUp Gold features powerful Layer 2/3 discovery which can be initiated from an IP Range Scan or SNMP Smart Scan of a core router’s Bridge Table to generate a detailed map of your network from top to bottom – so you can focus on keeping it running securely and at peak performance.
1 of 3 level 1, heading level 1
Map, inventory, and visualize your network topology and interdependencies
2 of 3 level 1, heading level 1
Document and track all your IT assets with enhanced inventory discovery
3 of 3 level 1, heading level 1
Troubleshoot connectivity issues with Layer 2 Trace and IP/ Mac Finder tools
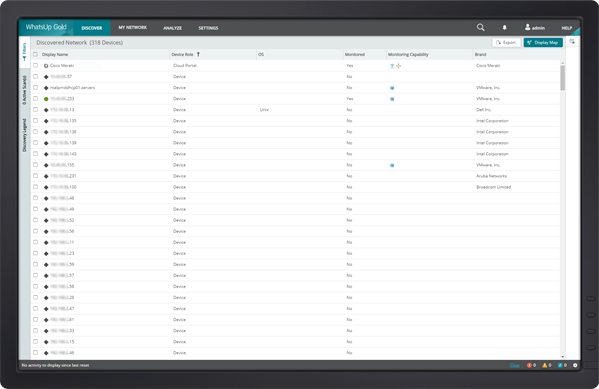
Discover Devices On Your Network
WhatsUp Gold uses a number of innovative Layer 2/3 discovery technologies–including ARP, SNMP, SSH, Virtual Infrastructure Management, IP addressing, ICMP and LLDP in combination with vendor-proprietary mechanisms – to discover everything connected to your network and build a complete and accurate picture of network devices and their port-to-port connectivity. Full or partial discoveries can be scheduled to run automatically or run on-demand.
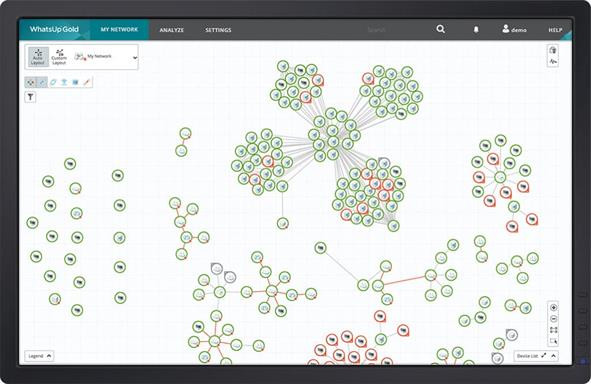
Visualize with Network Maps
WhatsUp Gold auto-generates integrated Layer 2 and 3 network maps that give you full visibility into physical, logical and virtual connectivity, including IP and VLAN-specific information. It dynamically updates its maps as changes occur in the network. Maps are easy to customize and manipulate so you can view your network the way you want. Learn more about network maps.
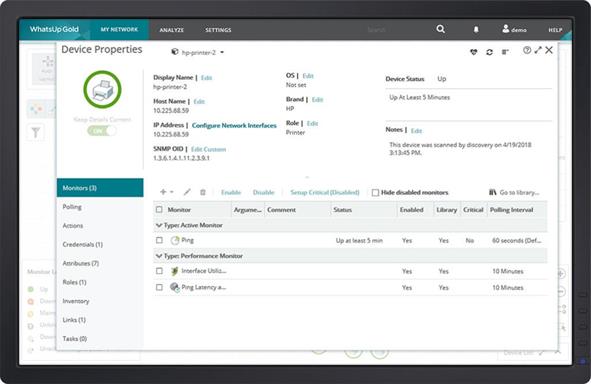
Assign Device Roles and Dependencies
At the completion of the discovery process, WhatsUp Gold automatically assigns devices roles that specify what data to collect and remedial actions that are enabled. You can easily modify default device roles and sub-roles or create new ones with the Device Role Editor. The discovery process also identifies dependencies that are marked on the map as directional arrows. With a couple of mouse clicks, dependency data can be used to suppress unnecessary alerts saving valuable troubleshooting time by minimizing false alerts.
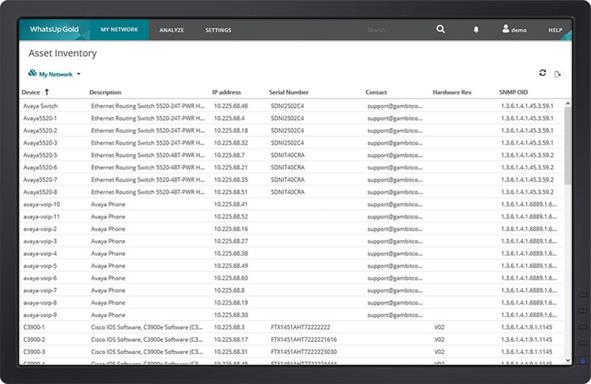
Maintain an Accurate Network Inventory
WhatsUp Gold provides comprehensive network inventory and configuration information – supporting the reporting/ documentation needs of your internal business process (such as ITIL) and regulatory requirements like PCI DSS, SOX, FISMA and HIPAA. Since you can easily export this information in CSV or Excel formats, your entire team will know exactly what resources are on your network, where they are and how they are connected at all times – even when your network grows, your office moves or datacenter resources get consolidated.
Manage Your Network Assets
Gather, filter and export a wide variety of inventory and configuration information across networking devices and systems.
- Networking Devices Asset Information: Manufacturer/Model, Serial Number, Hardware/Software/ Firmware Versions, Chassis/Module Inventory, Power Supplies/Fans
- Configuration Information: Interfaces, Bridge Ports, Switch Ports, VLANs
- Systems Inventory: All available system component details (CPU, RAM, disks, etc.), OS version & patch information, any installed software packages, support for automatic update of warranty information (Dell and HP) based on integration with their support websites
If You Can’t Find It, You Can’t Fix It
Even if you think you know where the network issue is, diagnosing it is likely going to depend upon what’s connected to it. A complete network discovery not only gives you an understanding of what’s connected to your network, it puts it all in context. Hard-to-diagnose problems like wireless APs that keep dropping signal suddenly become simple fixes when it’s clear that too many users are trying to connect at once.
Who’s Connected? Should They Be?
Security should be one of the top concerns of any IT team and that means knowing what’s accessing your network and why. If you don’t know what’s connected to your network you aren’t going to be able to identify insecure devices like rogue wireless access points that someone has shoved under their desk. You need to know where network access can be obtained and how – and you can’t do that without discovering what’s connected at all times.