Offers 8 technical controls that are key to passing file transfer compliance audits.
Security Key to Passing File Transfer Compliance Audits
Today's companies are dealing with an increasing array of legislative and industry requirements, mostly revolving around security. Legislation such as the Health Insurance Portability and Accountability Act (HIPAA), the Sarbanes-Oxley Act (SOX), the Gramm- Leach-Bliley (Act) GLBA, the Payment Card Industry Data Security Standards (PCI DSS), Basel II, and more all have stringent data security requirements for specific types of data within your business–often the data that forms the core of your business, such as customer information or financial data. Sometimes, these requirements are very technically precise. PCI DSS, for example, provides specific guidelines on what kind of data must be protected (customer and cardholder information), when it must be protected (in transit and when stored), and how it must be protected (encryption, in most cases). Other times, requirements are much more general and less technical in nature. HIPAA, for example, simply has a general requirement that patient information must not be disclosed to unauthorized parties; a 2009 addition to HIPAA also requires that data holders notify individuals when their protected information has been improperly disclosed. Those general business-level requirements can be extremely difficult to implement from a technology perspective. For example, suppose you work in the healthcare industry and are subject to HIPAA. You need to transfer certain patient information to a partner company, and you need to do so in a way that complies with HIPAA. That means you need to actually implement several technical controls:
- Encrypt the data while it is in storage
- Potentially encrypt the data during transmission within your company, especially if such transmission occurs over a publicly-accessible network (such as when accessed by telecommuting employees)
- Encrypt the data during transmission to your partner
- Securely wipe any temporary copies of the data created during transmission
- Keep track of every access to the data while it is stored
- Keep track of every transmission of the data
- Store that tracking information in a secure, tamperproof database or log
- Control who can initiate transfers of specific kinds of data
A Managed File Transfer (MFT) system can help with many of these requirements. By using a properly-configured MFT system as your sole means of transmitting data–potentially both within your organization and externally–you can become compliant with these requirements much more easily.
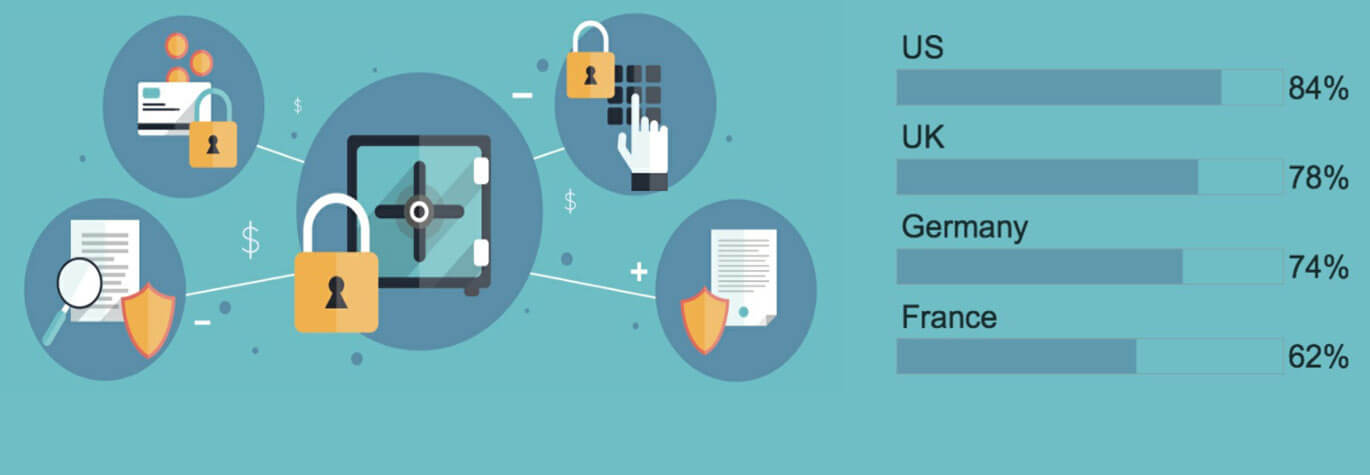
2016 State of Data Security and Compliance Report
Our 2016 survey of global IT teams is in. Find out how important they find data security and compliance and how they are mitigating the risk of data loss.

