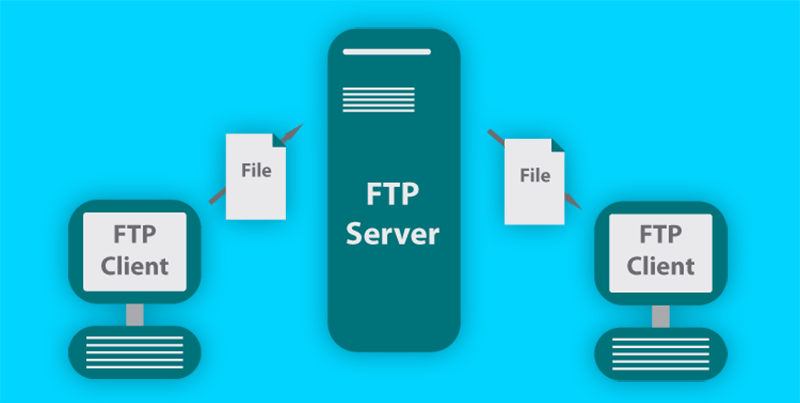
At its simplest, File Transfer Protocol (FTP) is a rudimentary method of moving files from one location on a network to another.
FTP traces back to the earliest days of networks (1971) predating even the emergence in the early 1980’s of modern Internet Protocol (IP) networks based on TCP (Transmission Control Protocol).
By far, FTP is the most popular way of moving files across the internet. Of the estimated 4.3 billion IP addresses in the IPv4 address space as of 2016, nearly 22 million were FTP servers. FTP servers can even be found imbedded in turnkey business applications and printers.
How does FTP work?
FTP works on a client/server model. Files are uploaded from an FTP client to an FTP server where they can be accessed by an application or client. The FTP server runs a daemon that continuously listens for FTP requests from clients.
When the FTP daemon receives a request, it sets up a control session which requests login details and then establishes the connection.
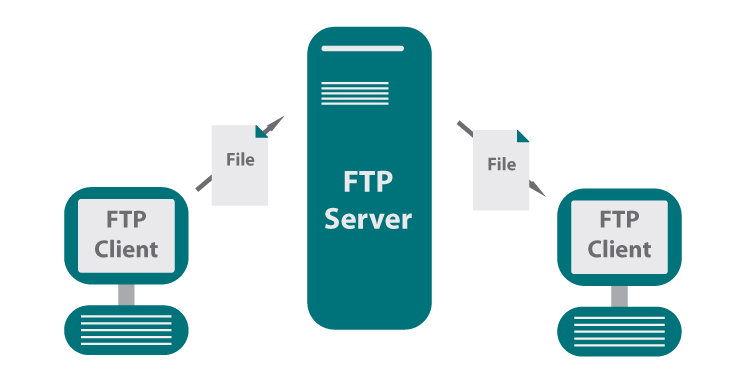
There are two types of login modes permitted by FTP. In Authenticated mode, the client needs to authenticate with a user id and password before it can gain access to the server. In the Anonymous mode, the client uses the account "anonymous" or "ftp" and provides an email address as the password. Once a control session is set up, the server will execute any of the above commands requested by the client.
Is FTP protocol a secure means of transferring data?
Simply put, no! The simplicity of FTP is its biggest weakness. It can be configured for access without valid authentication. Files are stored unencrypted and data transferred can be easily intercepted by hackers and cybercriminals as it traverses the open internet.
As of late 2016 there were still some 750,000 ‘anonymous’ FTP servers connected to the internet. These are low-hanging fruit to cybercriminals. With minimal effort, a control session can be established. By logging in with the account 'FTP' and an email address, they have full access to the directory of files uploaded and still resident on the server.
In March of 2017, the US FBI issued an alert to security teams in the healthcare industry to raise awareness of the risk posed by FTP servers containing Protected Health Information (PHI).
Need Encryption? Enter FTPS, SFTP and HTTPS.
Along the way, three options, Secure Sockets Layer (SSL), Secure Shell (SSH) and HTTPS, were added to FTP implementations. All three are heavily used to increase the security and reliability of file transfer by using encryption to protect against unauthorized viewing and modification of high-risk data during transmission across open networks.
FTPS
The fastest of the three and the most widely implemented option is FTPS, or FTP over SSL. FTPS secures files being transmitted through FTP with transport socket layer security (TLS). TLS is also sometimes referred to as SSL (it predecessor Secure Sockets Layer). FTPS requires separate control and transmission channels.
SFTP
SFTP (SSH File Transfer Protocol) provides file transfer and administration over a single channel (typically the SSH-2 protocol {TCP port 22}). It includes some extra features that allows resuming interrupted file transfers and the ability to remove files remotely. SFTP expects the underlying protocol (like SSH) to provide authentication and security.
HTTPS
HTTPS is a more secure version of HTTP. Much like how FTPS uses TLS encryption to transfer files. HTTPS has been around for a while, but was originally used for making payments over the web. As data privacy has become more important, it is deployed on many websites across several industries and required by Google to maintain good search rankings.
Do SSH, SSL, TLS and HTTPS make FTP secure?
SSH, SSL, TLS and HTTPS enable the secure transmission of data. In today’s threat landscape, however, it is important to consider that files are still stored in ‘plain text’ and that FTP servers configured in ‘anonymous’ mode provide an attractive attack vector to cybercriminals.
File transfer solutions have often been relegated to the darkest corner of the lowest wattage server room. It is not uncommon for IT teams to find long-ago deployed home grown FTP solutions that are not well understood, documented or easily maintained being used to manage company data. Files uploaded may never be deleted.
FTP servers also offer convenient command and control platforms for cybercriminals that have breached a networks security defenses. In the infamous Target breach, an internal FTP server was used to send the pilfered credit card data back to the cybercriminals servers.
Need More Layers of Security?
Not only is it important to encrypt data in transit, but it is equally important to protect and encrypt it ‘at rest’ on the file transfer server. Why? Two reasons. One, data exchange files are particularly vulnerable because they exist in a very easily-consumed format. Encryption adds a layer of protection that renders them unreadable by cybercriminals. Two, file transfer servers operate via a daemon that presents a constant attack vector to the open internet. They continuously ‘listen’ for someone trying to gain access.
Secure Managed File Transfer systems, like Ipswitch MOVEit, provide layers of security beyond SFTP, FTPS or HTTPS including encryption of data at rest, integration with your existing security infrastructure and logging of all file transfer activities to provide an automated audit trail.
Encrypt data ‘at rest’
Encrypting data stored on your transfer servers renders it unreadable to cybercriminals. PGP (Pretty Good Privacy) is a common approach which ensures encryption on upload without the requiring special skills on behalf of the user.
Integration with your existing security infrastructure
By integrating file transfer with existing security tools, you can enforce user, system, and file security policies while controlling the movement of sensitive files. This allows you to leverage user authorization/authentication, anti-virus, SIEM and DLP to further protect sensitive data.
Logging of all file transfer activities
With MOVEit, all data interactions, including files, events, people, policies, and processes, are logged in a tamper-evident database. This enables compliance with HIPAA, PCI, GDPR, SOX, FISMA, GLBA, FFIEC and other data privacy regulations.
Wrapping Up
As mentioned before, FTP by itself provides no additional security mechanism besides asking for a password. If the data you are sending is not considered sensitive and/or is restricted to transferring files within your network, then FTP can be perfectly fine to use. Don’t use this simplest form of FTP if sensitive data is being transferred outside your business network.
Which file transfer solution you use simply comes down to your budget, what you are transferring, and the type of encryption you need.