When considering what kind of logging you'll need, start with those internal and external needs as drivers.
Security & Compliance Driving Most File Transfer Logging Requirements
Many companies are incorporating external compliance requirements with their own internal needs. When considering what kind of logging you'll need, start with those internal and external needs as drivers. That said, there are a few general logging capabilities that most business will want:
- A tamperproof audit trail. Because nothing in technology can ever be "proof" against anything, you may see this positioned as tamper-evident instead, meaning that if tampering occurs, you'll at least know about it. This functionality is often implemented as a secure, and potentially encrypted, database in which the MFT solution stores records of transfer activity.
- Log accessibility. You'll need to report on transfer activity, and that means you'll need access to the log. Some MFT solutions will offer robust, detailed, built-in reporting, and others will provide direct read-only access to the database for use by third-party reporting tools. Ideally, you want both capabilities: Built-in reports get you up and running quickly, while database connectivity offers the ability to use external reporting, billing, and tracking applications.
- Who.Who transferred the file and who received it? The first who is often easy to determine for outgoing transfers, but you'll need an MFT solution that supports authentication, as well as non-repudiation, to log the identity of external senders and recipients. Non-repudiation is a feature that proves a file was received, and proves that it was not altered or corrupted while in transit. Who should also account for the physical servers involved, which can be authenticated through transport-level protocols such as SSL.
- What.Obviously, you'll want to know what was transferred. Typically, MFT solutions won't keep a copy of the file (although many can be configured to do so if you need an audit log that detailed, keeping a copy of the file can present additional security concerns), but they will log what file was transferred.
- When. When was the file transferred? When was the transfer complete? With large files, the difference between starting and completing the transfer can be significant–and you'll want to know both.
- Where. Where did the file come from? Where did it go? MFT solutions can often incorporate multi-step workflows that take a file through several steps, potentially involving transformation or translation, and each step should be clearly logged in the audit trail.
- How. How was the file transferred? What file transfer protocols were used? What encryption, if any, was used?
About the only thing you can't expect an audit log to include is why the transfer was made–although if you track the who, they can hopefully answer that question, if needed. But there's more that you should expect in the log: errors. File transfers aren't always smooth and problem-free, and a detailed activity and error log can make it easier for administrators to troubleshoot problems.
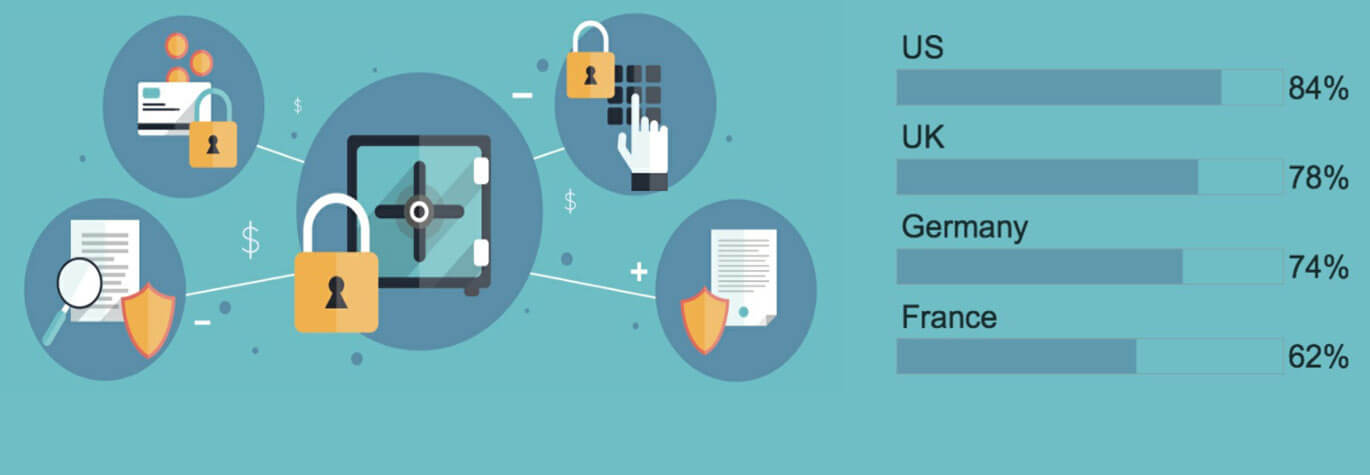
2016 State of Data Security and Compliance Report
Our 2016 survey of global IT teams is in. Find out how important they find data security and compliance and how they are mitigating the risk of data loss.

