How do we protect ourselves from rogue devices? What are the current solutions?
We’ve all seen TV shows and movies where industrious hackers remotely breach network perimeter defenses of government agencies with relative ease, retrieving data at will. We’ve also seen incidents where operatives break into premises and extract data directly from servers or workstations, gathering data over USB or Ethernet at speeds that far exceed those in the real world, where we are limited by the connector/cable type and related speed. I guess to do otherwise would make for boring viewing.
The devices used in these situations are rogue devices. They weren’t introduced or approved by IT, and their purpose is to bypass other cybersecurity controls such as firewalls, endpoint protection, and any other solution that protects the organization’s network.
Most cybersecurity professionals will agree that protecting against human actions is the most difficult of tasks, whether those actions are due to carelessness or malicious in nature. Rather than quote from surveys and white papers on the latest malware trends, let’s agree that we all know cybersecurity is an essential function and that reducing the risk of a data breach is a common goal for all organizations.
Don’t Dismiss Rogue Devices
There is no such thing as complete security, and it could happen to you. As cybersecurity solutions improve, it takes more work for cybercriminals to circumvent them. The insertion of a rogue device is considerably less work and is a highly effective attack vector if successful, ensuring a direct connection to a network or workstation. In other words, rogue device insertion is no longer limited to the intelligence community or high-profile targets but against all companies with attractive datasets. For cybercriminals, it’s a viable solution to the growing complexity of cybersecurity tools.
Cybercriminals are smart, organized, and sometimes state-sponsored. They can insert doctored devices into the supply chain for final delivery to target companies or organizations or simply use a local venue frequented by employees to dispense free gifts of chargers or promotional memory sticks with malware already installed. Their aim is to get the rogue devices onto the premises, and there are many options to choose from.
How Can IT Protect Against Rogue Devices?
The obvious security solution for Ethernet-based devices is to lock down DHCP or allow specific MAC addresses only, but what about USB devices?
As these devices are typically shown as HID (Human Interface Devices) and include mice, keyboard, cameras, chargers, and more, few cybersecurity solutions will detect these as a threat. Whether inserted by a careless or malicious user, a compromised USB device will perform its intended function once connected. This can include malware release (including ransomware) or data retrieval for broadcast or later collection.
The measures that IT can take are quite limited when it comes to physically preventing physical connection of rogue devices. Desoldering the connectors from motherboards is one option but obviously has productivity implications, not to mention voiding product warranties or risk of damage to multilayered PCBs. Similarly, the use of tamperproof labels is ineffective as it only provides a visual indication of tampering, and no alerts are sent to IT.
Coincidentally, almost as if I planned it, there’s a software-based solution that can detect rogue devices on the physical layer.
Sepio Systems is a security company specializing in rogue device mitigation and founded by cybersecurity experts from both private industry and government agencies. In February 2020, they were added to the U.S. Department of Homeland Security’s approved products list. I communicated with Yossi Appleboum, CEO at Sepio Systems Inc., to gain some insights.

Yossi Appleboum – CEO Sepio Systems Inc.
Image provided by Sepio Systems
Any comments to make on the no/low tech methods of rogue device detection available? These include desoldering connectors from motherboards or using tamperproof labels. How about locking down DHCP?
Similar to best practices in physical security, installing additional measures that could deter or discourage a possible attacker, and make him look for alternative targets, are always welcomed. As such, hard to remove labels and security paint marks (similar to those used for voiding warranty) could be helpful. “You don’t have to be Usain Bolt to outrun a tiger; you just need to be faster than the guy running next to you. So, in cybersecurity, it is not about 100% absolute security, which cannot be achieved; it’s about how you compare to other potential targets.”
Locking down DHCP or setting it up for specific MAC addresses is a basic security measure if you do not intend to go out and implement a full NAC [Network Access Control] solution.
What makes rogue device detection from external threats and malicious insiders difficult to handle in a traditional infrastructure?
The human factor is always the hardest one to tackle, think of it as a highly sophisticated Trojan, who can look to the sides when installing an implant or switching a mouse on someone’s desk. This “Human Trojan” can adapt and modify, striking where there is no “security coverage,” whether it’s a duct cable in a place where there are no CCTVs, or identifying that a certain endpoint is unattended and use the opportunity to connect something. The MAIN problem, though, are in the tools themselves as they appear to be authentic, impersonating as a legitimate keyboard or mouse, or by operating in the invisible L1 [Layer 1 or physical layer] of the network infrastructure. The “Clocking” capabilities, alongside an intimate acquaintance of the physical infrastructure and human criminal creativity, is what turns them into such a popular attack method.
What drove you to produce a technical solution that that detects and prevents access from rogue or unauthorized devices?
Sepio Systems is the third company that we’ve founded after working together for almost 30 years (the first two were successfully acquired by NASDAQ traded companies).
When our previous obligatory retention plan was coming to an end, we’ve started thinking about our next challenge, as our previous companies, we knew for sure that it would be cybersecurity-related, but we also knew that the market is heavily saturated with a lot of other cybersecurity companies. We’ve created a kind of a SWOT analysis to see where our expertise will have the strongest impact. We’ve been very familiar with rogue devices before, but during the “old days,” it was mainly affiliated with state-sponsored activities, but now it is no longer the case – as commercial Enterprises and critical infrastructure are being targeted as well.
Can you briefly explain how your solution works?
Our solution provides protection for two main interfaces – USB and Ethernet. These are the most popular attack interfaces (as in most cases, these interfaces, alongside the display port are the only one found on Endpoints/Thin clients).
Our detection algorithm is a combination of a physical layer fingerprinting, complemented by a machine learning module. We are constantly generating physical layer characteristics “signatures” or “fingerprints,” for every device that we encounter or get reports about. This part of the solution allows us to name the actual attack tool when we encounter it. The machine learning module kicks in for those “Known- Unknowns”, as new devices are introduced all the time, we cannot assume that we are familiar with, or have fingerprinted all devices, so the ML implementation provides the capability of detecting those Rogue Devices singularities.
Our solution, SepioPrime, uses its unique physical fingerprinting technology to discover and show you the inventory of visible and invisible hardware. It analyzes hardware behavior and automatically blocks attacks on peripheral devices (on host/hosts) and on network-level ports (on network switches).
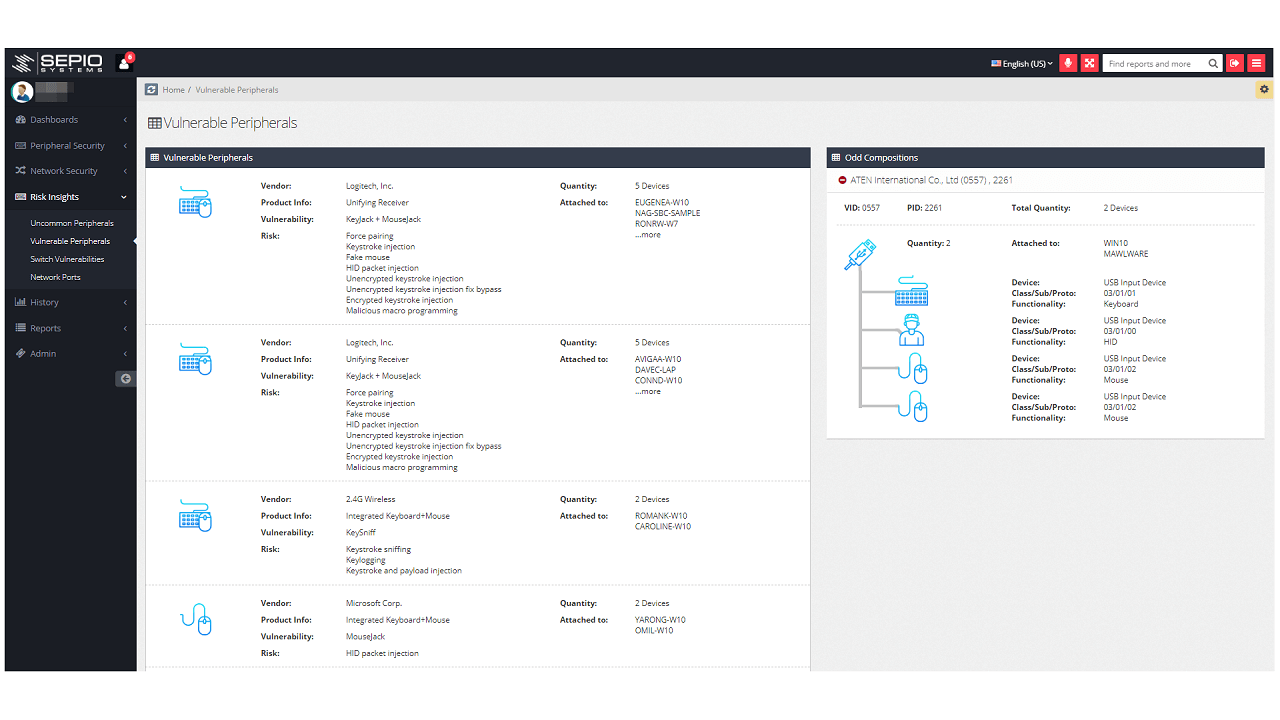
Dashboard screenshot showing vulnerable peripherals and their properties.
Image provided by Sepio Systems
According to default and easily configured policies, Sepio can block each USB port, which disables the rogue device in real-time as soon as it is connected.
Policies can be implemented all at once or in stages, such as to first implement inventory visibility, then risk visibility, and finally, gradual policy implementation.
Our network security module works at the physical layer, polling existing switches to analyze what’s happening at that layer and detecting all rogue devices plugged into the Ethernet network switches.
How are authorized devices detected (allowable memory sticks for example)?
As described previously, our solution allows the creation of flexible policies, according to users’ role or according to the enterprise risk analysis regarding what is an acceptable device and what is not. Once a policy is put in place and the devices were either approved or unapproved, any breach of policy will be handled according to the security scheme - a “soft” one, where just a notification will be sent, or a “harder” policy where the USB device will be blocked when a breach is detected. One of the key features, is the capability of detecting a legitimate device that has gone “bad”, due to a timed malicious activity, so that even when a device was previously authorized, once it goes “bad”, the solution understands that it is no longer a legitimate authorized device and will block it.
How important is physical security, (to the premises, server room and so on)?
Physical security has a crucial role in protecting the IT assets of the Enterprise.
Human beings, when paid-off or threatened to do something, become very resourceful, finding smart ways of gaining access to the IT/OT infrastructure. A lot has been talked about “silent cleaners”, “evil maids” and supply chain attacks. It’s not that the Physical security measures cannot by bypassed (you can find a variety of YouTube clips showing how to create a fraudulent access key for multiple products), it’s about making the life of the potential intruder harder, and maybe bring him to a point where he says “the hell with that, this place is like a fortress, let’s find another target”). Keeping your supply chain secured is a crucial factor as well, you need to know your sub-contractors, make sure that they are trustworthy and that each action that they take while on your premises is a legitimate one.
Do you have a favorite example or incident that demonstrates your solution in action?
A bank’s network infrastructure was compromised by using a MiTM attack by creating a virtual cable over a cellular network. This device created a VPN, in which the attacker could be located at a safe distance and manipulate any traffic that flows through that network connection. This device couldn’t be recovered by standard use of NAC/IDS because it operated on the physical layer, so that all that the networking monitoring solution could see was the original MAC address of the victim’s machine, while all the malicious traffic could be hidden from site. Only by probing the physical layer characteristics, one could identify the existence of such an implant, which is what we do successfully.
Is this a solution for small or medium-sized companies?
Although this solution applies to companies of all sizes, we’re focusing our efforts on mid-sized companies and larger Enterprises.
Any other comments on the future of rogue device detection?
We strongly believe that rogue device-based attacks will become more and more popular – we can already see it today when cybercrime organizations or state-sponsored actors evaluate their next potential target. They have the option of going head-to-head against existing cybersecurity products which are getting better or to find an alternative path into the enterprise’s crown jewels, and in that sense, the use of rogue devices provides them with a highly successful penetration path. Moreover, recent changes in the way we work are also supportive of such attacks. You have people working from home, without the physical security measures that they have in their enterprises – so a security officer can’t really control what is being connected at someone’s house. Furthermore, when people work from home, that means that there are less “suspecting eyes” around, so it’s easier to deploy HW-based attack tools. Since these types of attacks are on the rise, it is crucial to raise awareness.
Conclusion
Rogue devices are a possible avenue of attack for cybercriminals, and companies need to consider how they will handle the risk. Whether it’s connected networks or ‘air-gapped’ ones, cybercriminals can purchase the tools necessary to penetrate your network. These can include the Beagleboard (a system-on-a-chip solution about the size of a credit card) or USBNinja (looks like a typical USB charging cable but has remote Bluetooth capability). There are many other tools, and all they need is to deploy them on your premises. Have you considered the possibility?
