Two-factor authentication is currently one of the best security practices for protecting users, data and systems. Duo is one of the leading platforms for using two-factor authentication in the enterprise as it protects many common on-premises and cloud applications by default.
For on-premises authentication, Active Directory is still king and Duo integrates seamlessly on Windows to protect unauthorized logins to console and RDP sessions. To do this, Duo has a Windows software client to install which provides secondary authentication to Duo after the initial authentication to Active Directory.
In this article, I'll demonstrate some of the steps to setting up Duo for two-factor authentication on Windows.
Duo Admin Console
The first step is to create a new application in the Duo admin console to protect. The main purpose of this is to create an integration key, create a secret key, and obtain an API hostname. These are used in the Duo client software later on.
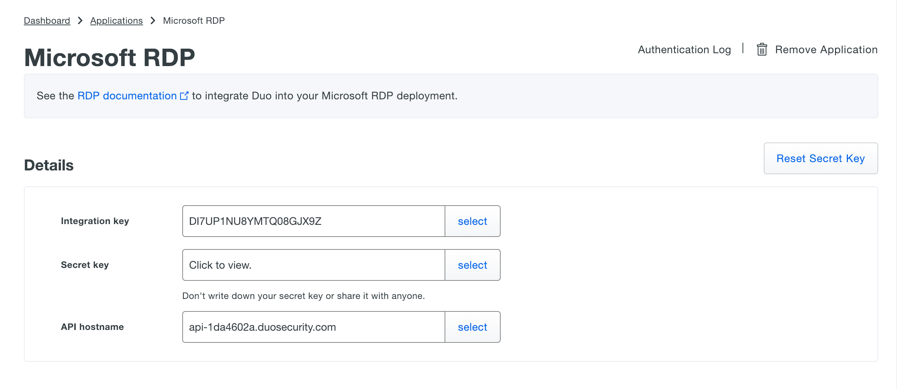
This page also gives you options to create user policies. For instance, you can set the username normalization policy so that DOMAIN\Username, username@domain, and username are all treated the same when logging into Windows with the Duo client software installed. Keep in mind that users must have the exact same username in Duo and in Active Directory for two-factor authentication to work correctly.
If the licensed being used allows, you can also configure only certain groups to authenticate to this application.
Run the Duo Windows Installer
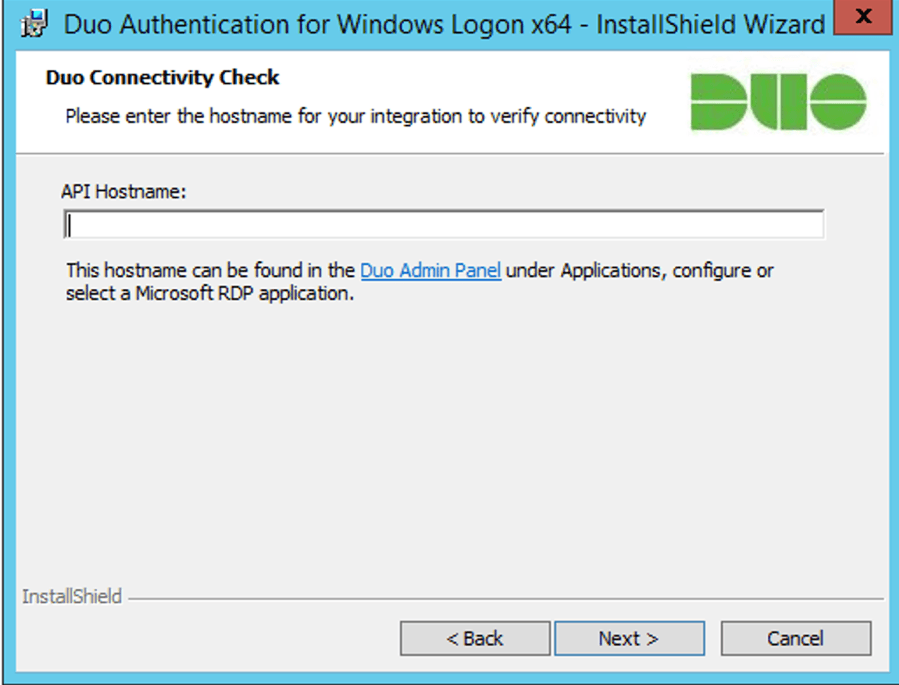
When running the installer for Duo authentication for Windows, the first thing you will be prompted for is the API hostname, which is obtained on the application page from the previous section.
Next you will need to input the integration and secret keys from the previous section as well.
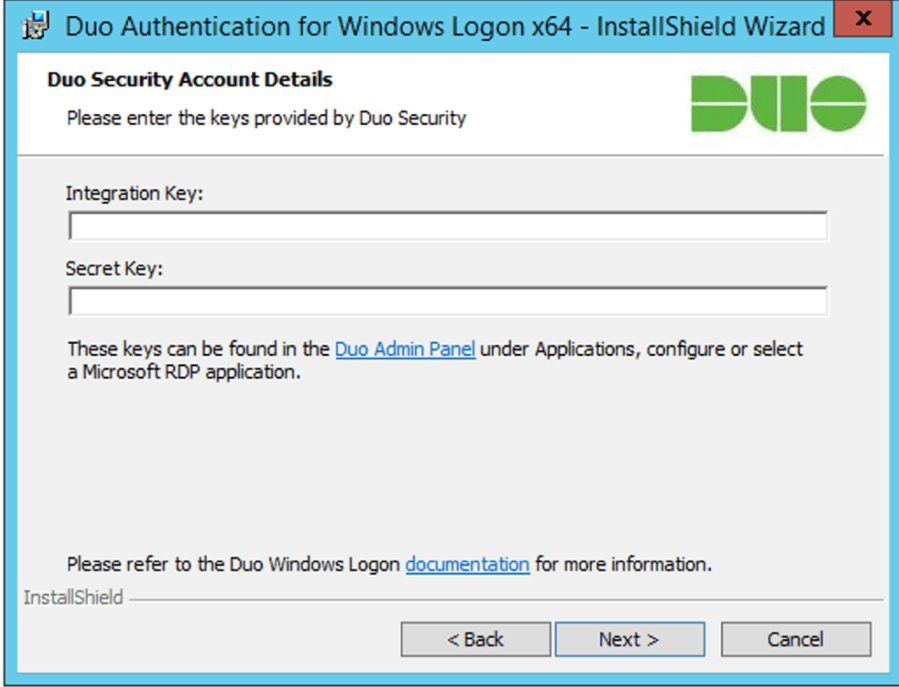
Finally, additional options can be used for the client software such as:
• Bypass Duo authentication when offline (FailOpen)
• Use auto push to authenticate if available
• Only prompt for Duo authentication when logging in via RDP
• Enable Smart card support
Testing the Windows Login
Now it's time to test out Duo on a Windows machine. I log-in as usual to my workstation (I could also use RDP), but after I enter my username I am prompted with the following message:
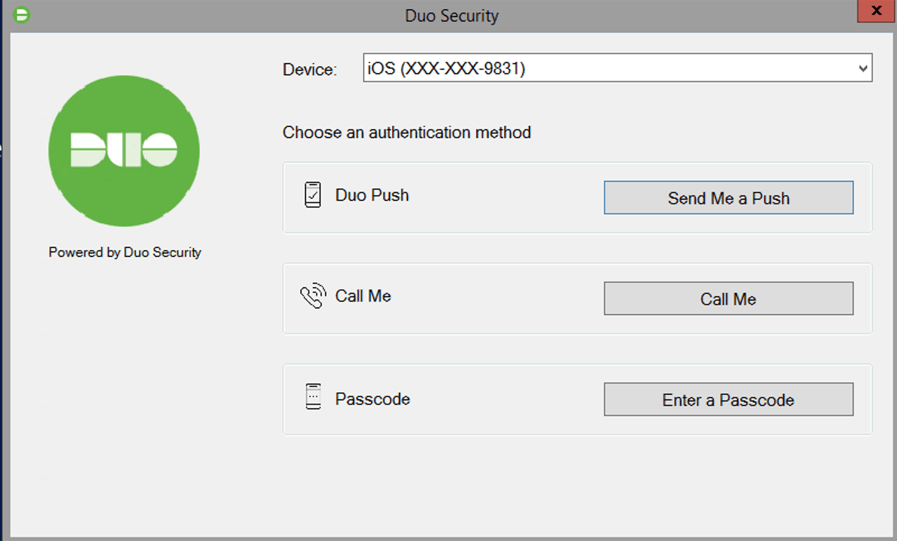
Depending on the Duo policies configured, a user can send a Duo push, call or enter a passcode in order to perform the secondary authentication for two-factor authentication.
A Duo push, means that a prompt will be send to accept on a mobile device configured for Duo, such as an iPhone. The “Call Me” option means that a number will be called by Duo, and the user will need to accept the call and press a key. The “Passcode” option is for when an authenticator app like Duo provides a temporary passcode for the user to enter.
Although there have been increases in hacking two-factor authentication, enabling this in an enterprise still provides a great layer of protection in the security scheme. Using Duo makes 2FA deployment in Windows a manageable task due to its integration with so many applications and platforms.
