Healthcare companies in the US have had to protect sensitive personal data for a long time to satisfy HIPAA compliance rules. But are healthcare companies on the hook in light of the GDPR?
Under HIPAA (Health Insurance Portability and Accountability Act), companies are required to secure all protected health information (PHI) and electronic protected health information (ePHI) at rest and in transit. But do healthcare companies need to be compliant with the EU's GDPR (General Data Protection Regulation) if they are already HIPAA compliant? Also, what duplication of operational effort can be avoided when complying with both GDPR and HIPAA guidelines?
Complying with HIPAA is a start, but GDPR covers more types of information, with tighter boundaries around what can be done with it. For a deeper dive, check out this overview on GDPR and the seven principles that define it.
HIPAA and GDPR Compliance
 First, let’s focus on who needs to comply with the GDPR. If you’re a healthcare company in the US there is no denying that your business must be HIPAA compliant. But what if your business doesn’t handle
personal data in the EU? Do you even need to comply with the GDPR? Short answer: it depends.
First, let’s focus on who needs to comply with the GDPR. If you’re a healthcare company in the US there is no denying that your business must be HIPAA compliant. But what if your business doesn’t handle
personal data in the EU? Do you even need to comply with the GDPR? Short answer: it depends.
The most obvious reasons that a US healthcare organization would have to comply with GDPR would be medical tourism programs, or providing clinical services internationally within the boundaries of the EU. Medical tourism is the act of traveling internationally to receive medical care.
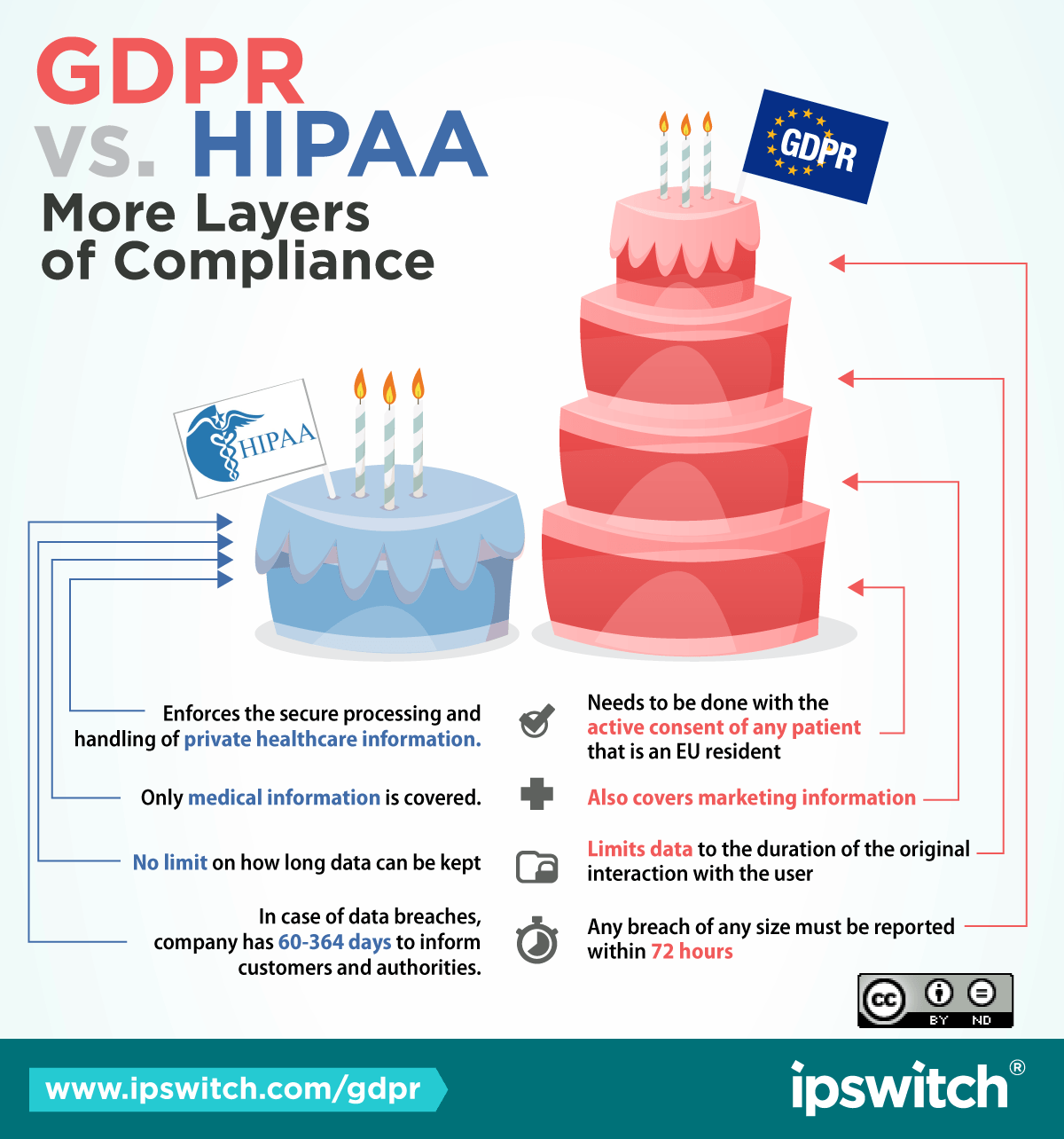
So what if a healthcare provider provides services to an EU resident within the US? Would the healthcare company then have to comply with the GDPR? In this circumstance, the HIPAA Privacy Rule and HIPPA Security Rule would enforce the secure processing and handling of private healthcare information. Therefore, those measures of data protection would already be in place regardless.
In the occurrence that the personal information of an EU resident is collected by a healthcare provider within the US, that healthcare provider would not necessarily have to comply with the GDPR. If that data was collected while the person was in the EU, then the GDPR would apply. The best example is if a business collects personal information of someone on a website that is residing in the EU. This isn't entirely necessary, but companies would rather be safe.
The biggest difference between HIPAA and the GDPR is that the GDPR covers persons in the EU regardless of citizenship, while HIPAA only protects ePHI and PHI handled by businesses within the US.
Active Consent Under GDPR vs. HIPAA
Healthcare providers already ensure the secure processing and handling of PHI or ePHI under HIPAA, but under the GDPR this will need to be done with the active consent of any patient that is an EU resident. The big word here being “consent.” HIPAA doesn’t require active consent.
It’s also important to note that the GDPR effects marketing data as well, so this doesn’t necessary have to be a case of an EU resident seeking medical services from a US healthcare company. An EU resident needs to give explicit consent to opt into any communication whether it be email, phone, etc. For example, if your business has a blog subscription form or a medical product form on your website, you need to cover all your bases in regards to asking for explicit consent.
You will also want to make sure all forms on your website link to your privacy policy. It goes without saying, that you would be wise to include more information about how your business controls and processes data in your privacy policy.
Right to Be Forgotten
Right of erasure, or the right to be forgotten as it is also known, is a huge obstacle brought on by GDPR requirements. Under Article 17 of the GDPR, all EU residents have the right to ask any business controlling and storing their data to erase it and all backups without exception. HIPAA does not cover this, so healthcare organizations in the US working with EU residents will need to have the ability to locate and delete all data pertaining to EU residents.
The GDPR regulations are very specific about this. If a former patient, customer, or business partner that you've done business with in the EU comes to you and asks for their personal data to be removed, you must comply. That person does not need to tell you why either.
Personal data under the GDPR includes the following and is found in the Definitions of Article 4:
"‘personal data’ means any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person;"
 This means IT in any healthcare organization that controls personally identifiable information (PII) will need the ability to remove every record, backup, or data on any device or server immediately. Not doing so could
expose your business to civil suit, or even worse non-compliance. Penalties for non-compliance could cost your business 4% of annual turnover or 20 million euros, whichever is more. There is no exception for any company in any industry, including
healthcare.
This means IT in any healthcare organization that controls personally identifiable information (PII) will need the ability to remove every record, backup, or data on any device or server immediately. Not doing so could
expose your business to civil suit, or even worse non-compliance. Penalties for non-compliance could cost your business 4% of annual turnover or 20 million euros, whichever is more. There is no exception for any company in any industry, including
healthcare.
So what if you store that data in the cloud with 3rd party cloud services like AWS or Windows Azure? Well, you will need to know how they handle that data as well. We can assume that AWS and Azure are compliant (though it wouldn’t hurt to double-check), but what about those smaller 3rd party solutions? You will need to get assurances from them that they will handle and secure all sensitive data the same way and in a GDPR compliant manner.
Handling Data Breaches - HIPAA vs. GDPR Requirements
Data breaches are the norm in this day and age, so it would be quite concerning, to say the least, if you don’t already have a policy in place to properly deal with data breaches and data loss. HIPAA is very implicit about breach notification, so as a healthcare company in the US you are already required to notify all individuals who are affected by a data breach.
If more than 500 individuals are affected then you need to let the Office for Civil Rights (OCR) know and all individuals affected within 60 days. Smaller breaches, you must notify the OCR and those affected on the final day of reporting each year, which is March 1st the following year. For instance, for any minor data breach in 2017, you had until March 1, 2018 to notify those impacted.
Under HIPAA, a data breach is defined as unauthorized exposure of ePHI or disclosure that’s not authorized or allowed under the HIPAA Privacy Rule. The breach rules were updated in 2013 by the HITECH Act.
Of course, the obvious difference is that HIPAA compliance only covers the handling of healthcare data in the US, while the GDPR covers all personal data within the EU. However, the most important aspect of data breaches under GDPR is how you report a data breach. As noted above, under HIPAA depending on the size of the breach you may have a different option on when to report it. This isn’t the case with GDPR.
The definition of a data breach under the GDPR guidelines differs in that it is only considered a breach if the data stolen or loss infringes on the rights of the individual affected. To eliminate any confusion, here is the exact verbiage from the GDPR in Article 33:
“In the case of a personal data breach, the controller shall without undue delay and, where feasible, not authority competent in accordance with Article 55, unless the personal data breach is unlikely to result in a risk to the rights and freedoms of natural persons. Where the notification to the supervisory authority is not made within 72 hours, it shall be accompanied by reasons for the delay.”
Under Article 33 of the GDPR, every breach must be well documented and sent to a supervisor authority. A supervisor authority is an independent public authority that monitors and determines if an entity or business has remained complaint. The full definition of a supervisor authority is found in Article 51.
This leaves some questions as to whom non-member states, such as the US have to report to. You must report to a supervisory authority in the state that the data is processed. In the case of US healthcare companies, companies will have to deal with the painstaking task of choosing between a plethora of supervisory authorities. It’s not as cut and dry for those outside the EU, so this will need to become clearer once the GDPR is enacted on May 25, 2018.
Guidelines for Encrypting Personal Data
 Encrypting private and personal data in transit is already covered under HIPAA, but surprisingly many healthcare organizations still struggle to implement proper data protection processes. Employees still lack security training and shadow IT is rampant in the healthcare sector. This could be as innocent as uploading
a patient record to Google Drive to share with a doctor. It’s easy and quick to implement, but the problem is that IT and the security team trying to maintain compliance
can’t control and protect that data.
Encrypting private and personal data in transit is already covered under HIPAA, but surprisingly many healthcare organizations still struggle to implement proper data protection processes. Employees still lack security training and shadow IT is rampant in the healthcare sector. This could be as innocent as uploading
a patient record to Google Drive to share with a doctor. It’s easy and quick to implement, but the problem is that IT and the security team trying to maintain compliance
can’t control and protect that data.
Many companies are learning the hard way by receiving hefty fines when they get caught by auditors. If your organization hasn’t taken the time to look at a solution for secure managed file transfer, you should start now. This isn’t even for the sake of GDPR—You are already required to encrypt data transfers under HIPAA.
Another tool that should be in your IT arsenal is cyber security software, like netwrix auditor that can help analyze user behavior and mitigate risk within your IT infrastructure.
Furthermore, it’s always wise to get a risk assessment of your business. This will allow you to identify any hazards and evaluate whether or not you need to implement specific security controls. This may include updating medical care data systems or simply training employees on the security risks surrounding medical data.
Better Safe than Sorry
Ok, so you don’t process the data of residents in the EU, and you are strictly a US-based healthcare company. You’re probably thinking that none of this concerns you. Well, it might not right now, but that may soon change. With how the government and US Congress are reassessing how PII should be handled. States are already implementing their own compliance rules that are similar to the GDPR. It’s only a matter of time until you need to have those safeguards in place, so why not get a head start and start preparing now? The alternative is going out of business from hefty fines and civil suits.
Ultimately, the compliance rules are going to change. A lot of what the GDPR will require of businesses outside of the EU needs to get ironed out in the court systems. In time we will have more specific answers.