File Transfer & Information Security Blog
Featured Articles

-
6 Advantages of Single Sign-On and Why Your Business Needs It
Doug Barney | | Automation | File Transfer | Security
You probably have heard the saying "practice makes perfect" countless times, but in situations where there's nothing to perfect, repetition gets boring and tedious with time.
-
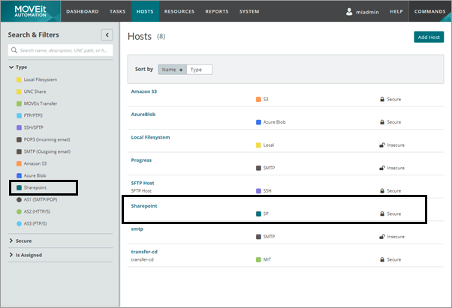
Best Practices For Safe, Compliant And Convenient SharePoint File Transfer
Doug Barney | | File Transfer | Security
Well over 200,000,000 people across 250,000-plus organizations use Microsoft SharePoint. That's a lot of data and a lot of files. SharePoint is arguably the most common document library software in use today.
-
Managed File Transfer & PCI DSS Compliance
Sometimes we do things not because we want to but because we must. While there's often a temptation to violate regulations and "test the waters," deep down, we feel relieved because we know we're on the good side of the law, and that's what matters. One word for that: ...
-
SSH File Transfer Protocol 101: What It Is and When to Use It
David Perez | | File Transfer | IT Insights
Picture this: "Webhosting Company loses 13 million plaintext passwords" in bold at the head of a blog or a paper.
-
Is the Biggest Risk to Data Security in Healthcare Often the Most Overlooked?
Protecting data in any healthcare organisation is no easy feat. Healthcare providers and their partners must balance protecting patient privacy with delivering effective patient care whilst simultaneously meeting strict regulatory requirements around data privacy.
-
What's New in MOVEit 2021
Progress recently released MOVEit 2021, adding an impressive list of enhancements to its award-winning secure and managed file transfer solution.
-
Getting to the Bottom of GDPR – the Expert View From Osterman Research
When GDPR came into effect three years ago, it only impacted companies somehow doing business with Europe. While that encompasses a large swath of businesses, many enterprises had nothing to worry about.
-
Managed File Transfer Key To Business Resilience
Every business nearly every day and often all day long uses "file transfer" to move or, as some would say, transport data from one point to another.
-
Boost Security and Workflow with Automation
Four words: data on the move. Businesses today completely rely on being able to send, receive and share data, often incredibly large batches of data, quickly and securely.
-
Managed File Transfer and Improving Regulatory Compliance
Evan Kirstel | | Security
Learn how MFT software was used in the healthcare sector for transferring huge amounts of data on a daily basis while maintaining security & compliance.
-
4 Predictions for Managed File Transfer 2021
Alexandra Cassandro | | IT Insights
Multiple integrations, migration to cloud & mobile, BizOps, focus on security & encryption – these are just some of the priorities in file sharing for 2021.
-
Managed File Transfer - What is it?
Doug Barney | | Security
No matter which industry sector your business operates in, facilitating collaboration among your employees, customers and business partners is a key factor in driving business process efficiencies and increasing your revenue generation potential. Collaboration requires...
-
Ways to Ensure Data Protection and Secure File Sharing of Personal Data
Alexandra Cassandro | | Security
In today's age of the Internet, our personal data are stored on various servers, and they are continuously moving around. We need to realize how are the data handled, why it is like that, and how the process for data protection can be improved. Is there anything we can...
-
Just Released: Managed File Transfer for Dummies
Alexandra Cassandro | | IT Insights
Progress MOVEit recently released a special edition eBook, Managed File Transfer For Dummies! This familiar, easy-to-read eBook conceptualizes managing file transfers in today's borderless enterprise while reducing risk and ensuring compliance in just five-short...
-
Find Inactive User Accounts In Your Domain
Active Directory is a directory service that maintains information about users, computers and related objects. Here is how you can find inactive user accounts.
-
UNIX Has Always Been More Secure Than Windows
Robert Yeckley | | IT Insights | Security
By default, UNIX-based systems are inherently more secure than the Windows operating system. In this article, we describe precisely why that is.
-
MFT as a Dropbox Alternative for Business File Transfer
Alexandra Cassandro | | IT Insights
A countless amount of data is being processed through the internet every single day (and every hour, minute, second, millisecond) of that day. And, given our current climate, sharing files over the internet is more important than ever. You're probably sharing jpegs,...
-
Are Free File Transfer Tools Bad?
Alexandra Cassandro | | IT Insights
We all love free stuff, right? But sometimes, those freebies you find online can be too good to be true. Free file transfer tools are no different.
-
What Is Cloud Data Integration?
Greg Mooney | | Cloud | IT Insights
When everyone on a business team has access to all the data the individual members handle, the team is better positioned to achieve its corporate objectives.
-
Fast and Flexible SharePoint Workflows with MOVEit 2020.1
Mark Towler | | File Transfer | Security
Thanks to input from MOVEit users the latest release includes also: Expanded Single Sign-On (SSO), MS SQL 2019 Support, Gateway Multi-Org Support & more!